
Various notes and key takeaways from the THM room John The Ripper.
https://tryhackme.com/room/johntheripper0
John is different from tools like hydra. Hydra does blind bruteforcing by trying username/password combinations on a service daemon like ftp server or telnet server. John however needs the hash first.
Useful Commands
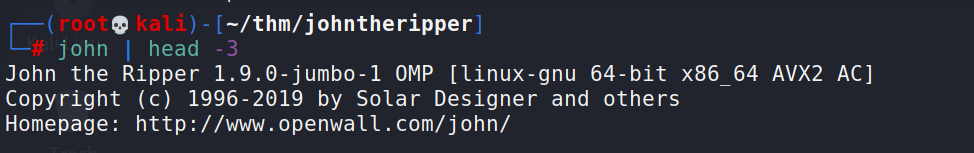
Quick way to check the version running on your system.
# john | head -3
NTLM Hashes
You can acquire NTHash/NTLM hashes by dumping the SAM database on a Windows machine, by using a tool like Mimikatz or from the Active Directory database: NTDS.dit.
You may not have to crack the hash to continue privilege escalation- as you can often conduct a “pass the hash” attack instead, but sometimes hash cracking is a viable option if there is a weak password policy.
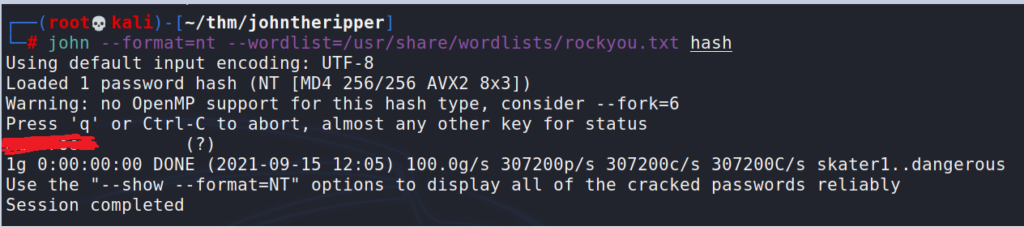
Once we have saved the hash in a file (in our case also called hash) we can use john to crack NT hashes.
# john --format=nt --wordlist=/usr/share/wordlists/rockyou.txt hash
Note
A Pass-the-Hash (PtH) attack is a technique whereby an attacker captures a password hash (as opposed to the password characters) and then simply passes it through for authentication and potentially lateral access to other networked systems. The threat actor doesn’t need to decrypt the hash to obtain a plain text password. PtH attacks exploit the authentication protocol, as the passwords hash remains static for every session until the password is rotated. Attackers commonly obtain hashes by scraping a system’s active memory and other techniques. https://www.beyondtrust.com/resources/glossary/pass-the-hash-pth-attack
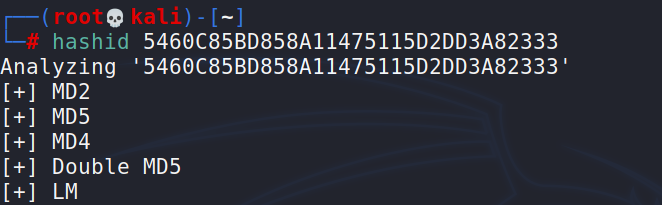
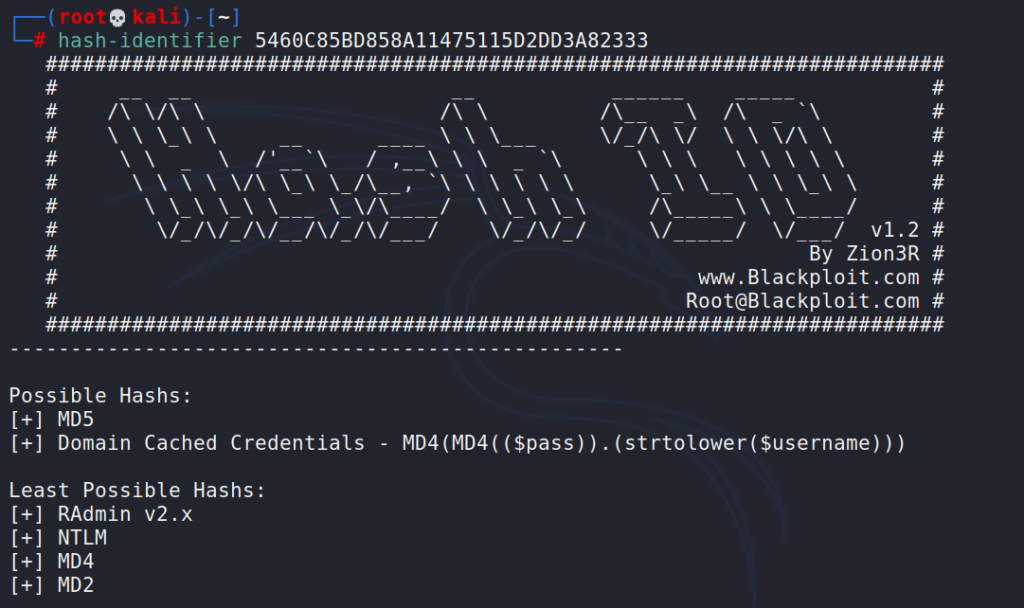
If we are not sure about the hash format, we can use hashid/hash-identifier. Both come preinstalled in Kali.
hashid
hash-identifier
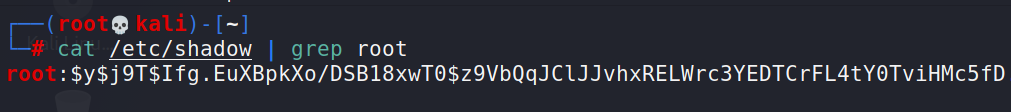
etc/shadow Hashes
The /etc/shadow file is the file on Linux machines where password hashes are stored. It also stores other information, such as the date of last password change and password expiration information. It contains one entry per line for each user or user account of the system. This file is usually only accessible by the root user- so in order to get your hands on the hashes you must have sufficient privileges, but if you do- there is a chance that you will be able to crack some of the hashes.
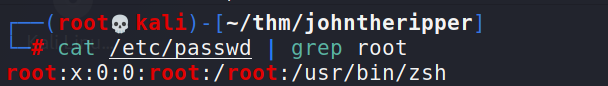
Unshadow
Is a tool built into the John suite of tools. The unshadow command will basically combine the data of /etc/passwd and /etc/shadow to create 1 file with username and password details. Usage is quite simple.
unshadow [path to passwd] [path to shadow]
Save both the /etc/shadow and /etc/passwd outputs to files.
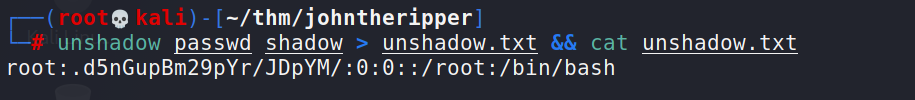
# unshadow passwd shadow > unshadow.txt && cat unshadow.txt # john --format=sha512crypt --wordlist=/usr/share/wordlists/rockyou.txt unshadow.txt
Format may vary, use –format=”value”

Similar to unshadow, John suite supports a plethora of tools like ssh2john, zip2john, rar2john. All tools included in John can be found at /usr/share/john/
Syntax
# python ssh2john.py /root/Desktop/idrsa.id_rsa > /root/Desktop/id # zip2john /root/Desktop/file.zip > /root/Desktop/ziphash.txt # rar2john /root/Desktop/file.rar > /root/Desktop/rarhash.txt
Once we have the hashed output we can use John in combination with a wordlist to try and crack the hash.
# john --wordlist=/usr/share/wordlist/rockyou.txt /root/Desktop/id
Single Crack Mode
This is the mode you should start cracking with. It will use the login names, “GECOS” / “Full Name” fields, and users’ home directory names as candidate passwords, also with a large set of mangling rules applied. Since the information is only used against passwords for the accounts it was taken from (and against password hashes which happened to be assigned the same salt), “single crack” mode is much faster than wordlist mode. This permits for the use of a much larger set of word mangling rules with “single crack”, and their use is always enabled with this mode. Successfully guessed passwords are also tried against all loaded password hashes just in case more users have the same password.
Note
The gecos field, or GECOS field is a field of each record in the /etc/passwd file on Unix, and similar operating systems. On UNIX, it is the 5th of 7 fields in a record.
The colon between the values is what specifies a “GECOS field”,
Syntax is similar with the one we have seen so far.
# john --single --format=raw-md5 hashes.txt
If you’re cracking hashes in single crack mode, you need to change the file format that you’re feeding john for it to understand what data to create a wordlist from. You do this by prepending the hash with the username that the hash belongs to. For example hash
1rt23x3cdcb96d98ud48ccc7b8666033
would be
ilsa:1rt23x3cdcb96d98ud48ccc7b8666033
Custom Rules
This option translates to being able to create custom rules and dynamically generate passwords tailored to each occasion, which is particularly useful since many organizations require a certain level of password complexity to try and combat dictionary attacks. Basically custom rules allows us to exploit the password complexity predictability.
Rule sets get placed in the bottom of the config file which can be found at /etc/john/john.conf.
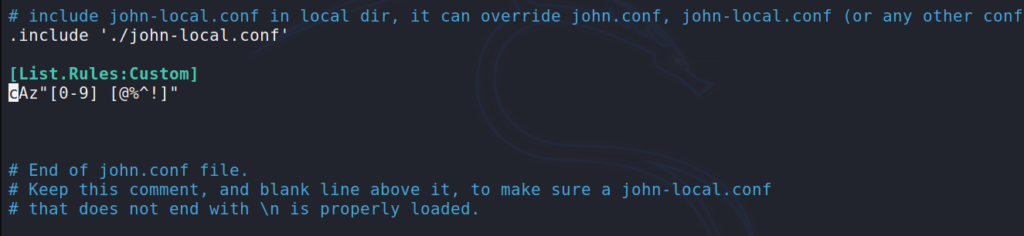
Syntax
The most common commands are
- c : Capitalizes the letter
- $X : append character X to the word
- ^X : prefix the word with character X
- d : Duplicate the word, i.e “custom” -> “customcustom”
- Az : Takes the word and appends it with the characters you define
- A0 : Takes the word and prepends it with the characters you define
[0-9] – Will include numbers 0-9
[0] – Will include only the number 0
[A-z] – Will include both upper and lowercase
[A-Z] – Will include only uppercase letters
[a-z] – Will include only lowercase letters
[a] – Will include only a
[$%!@#] – Will include the symbols $%!@#
Detailed walkthroughs and documentation can be found at the following links.
https://www.openwall.com/john/doc/RULES.shtml